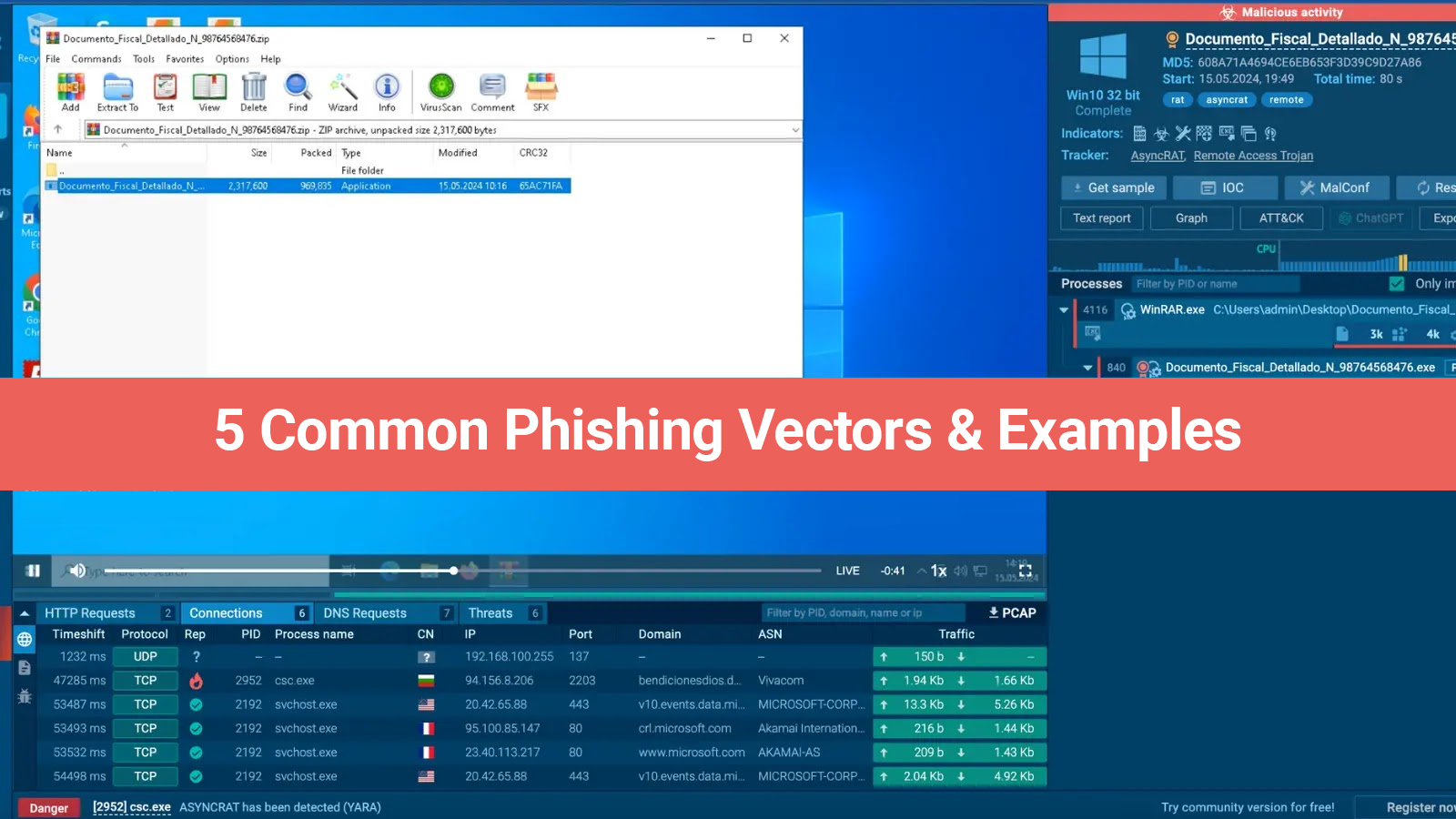
With its use of double extortion, Ransomware-as-a-Service (RaaS) distribution, and unusual payment methods, Akira is quickly emerging as one of the most prolific ransomware families.
The Akira ransomware group seems to have ties to the now-defunct Conti ransomware gang, according to a report that examined source code and blockchain data. Conti, a highly infamous ransomware family in recent times, is thought to have sprung from the highly targeted Ryuk ransomware, another widespread ransomware family.
Organizations must improve their cybersecurity posture to effectively fight complex threats as ransomware attackers develop more sophisticated ransomware families, alter their techniques, and hurt enterprises' finances and reputations. This paper highlights the Akira ransomware family, which is directed by operators with a high level of expertise & skill.
Things that Organizations Must Know about Akira Ransomware
The Akira ransomware first surfaced in March 2023 and has been observed to target US and Canadian-based businesses. According to a Sophos investigation, the Tor leak site has a distinctive retro appearance that is evocative of “1980s green-screen consoles” that hackers may use by typing particular commands. Though they both append encrypted files with the same “.akira” extension, the Akira ransomware family that was active in 2017 is not at all based on the code.
The code similarities between the two ransomware families can be explained by the association between Akira operators and Conti ransomware actors, as was previously revealed. The Akira ransomware and the Conti ransomware had coding similarities, according to a July assessment by the Arctic Wolf Labs Team. It's even harder to link ransomware families to Conti operators since, as they also pointed out, several criminal actors utilized Conti's disclosed source code to modify or construct their malware.
An investigation suggests that Akira is derived from the Conti ransomware: It avoids the same file extensions as Conti does and uses comparable algorithms to Conti. We think that financial gain is the primary driving force behind Akira operators' targeting of organizations.
Before encrypting devices and files, the Akira RaaS organization uses double extortion tactics and takes the victims' vital data. It's interesting to note that reports state that Akira operators provide victims the choice to pay for data erasure or file decryption; they do not compel victims to pay for both. Reports state that the usual range of ransom demands for Akira is between US$200,000 to more than US$4 million.
Akira attacks were announced as a security alert to the healthcare industry by the U.S. Department of Health and Human Services Health Sector Cybersecurity Coordination Center (HC3) on September 12, 2023.
Top Affected Countries & Industries
Compared to other more well-known and often used ransomware families, Akira is a relatively new threat that is highly targeted, so the quantity of attacks is not as great. With 53.1% of all detections, our Trend MicroTM Smart Protection NetworkTM telemetry indicates that France was the country most affected by Akira between May 1, 2023, and August 31, 2023. With 107 and 22 detections, respectively, the United States and Turkey occupy the second and third positions.
Figure - Nations with the most Akira ransomware attack attempts per machine (May 1, 2023, to August 31, 2023).
Source: Trend Micro Smart Protection Network Infrastructure.
Our analysis indicates that unnamed industries account for the majority of Akira's victims. Approximately 80% of Akira's victims are Small and Medium-Sized Businesses (SMBs), according to sources. During the three months, the manufacturing, financial, and materials sectors were among the top five.
Figure - Sectors with the greatest volume of Akira ransomware attack attempts per machine (May 1, 2023, to August 31, 2023).
Source: Trend Micro Smart Protection Network Infrastructure.
In June 2023, people around the world saw a spike in Akira's monthly detections with 508 assault attempts, a number that is noticeably greater than any other month during our analysis period. Only three assault attempts were detected during the entire month of May 2023, which was our lowest detection rate.
Figure - Monthly summary of Akira ransomware detections by machine (May 1, 2023, to August 31, 2023).
Source: Trend Micro Smart Protection Network infrastructure.
Targeted Industries & Regions: According to Akira's Leak Website
We now turn our attention to the data that the operators of the Akira ransomware have leaked, which includes information on the companies that Akira actors have targeted. Based on a combination of Trend Micro's Open-Source Intelligence (OSINT) analysis and the leak site investigation, this data indicates that 107 enterprises were infiltrated by Akira ransomware perpetrators between April 1, 2023, and August 31, 2023. Eighty-five percent of the victims of Akira were North American businesses.
Figure - The victim organizations of the Akira ransomware and their distribution per region.
Sources: Akira Ransomware’s Leak Website & Trend Micro’s OSINT Research (April 2023 – August 2023).
Figure - The top ten nations that the Akira ransomware organization has hit.
Sources: Akira Ransomware’s Leak Website & Trend Micro’s OSINT Research (April 2023 – August 2023).
We discovered that, out of the 59 victims of Akira, the majority were small firms with one to two hundred people. Large corporations and midsized companies occupied the second and third places, respectively. Interestingly, according to statistics from leak sites, the industries most targeted are those in academia and professional services, closely followed by materials and construction.
Figure - The breakdown of victim organizations of the Akira ransomware by organization size.
Sources: Akira ransomware’s Leak Website & Trend Micro’s OSINT Research (April 2023 – August 2023).
Infection Chain & Techniques
Usually, the Akira ransomware enters victim environments by utilizing legitimate login credentials that it may have acquired from other attacks or its affiliates. Third-party applications including Windows Remote Desktop Protocol (RDP), AnyDesk, Radmin, WinRAR, PCHunter, AdFind, PowerTool, Terminator, Advanced IP Scanner, and Cloudflare's tunneling tool have all been used to watch it. Figure 8: The infection chain of Akira.
Akira's Attack Playbook
- Credential Compromise: Your passwords that have been stolen may be your point of entry.
- Double Extortion: To begin with, encryption weakens your systems. A second ransom demand follows from stolen data that has been leaked.
- Global, but US-Centric: There are targets all across the world, but US policy has focused strikes on particular areas.
Tactics, Techniques, and Procedures (TTPs)
- Common vulnerabilities are frequently exploited by Akura to gain initial access to networks.
- After entering, lateral movement strategies lead to the information they wish to exfiltrate and encrypt.
Healthcare businesses desperately need comprehensive protection plans and deeper threat intelligence.
Akira's Recent Activities
Three months after Akira's discovery, in June 2023, it added Linux computers to its list of targeted systems. Malware expert Rivitna revealed on X that Akira ransomware perpetrators targeted VMware ESXi virtual computers using a Linux encryptor.
Meanwhile, Akira was reportedly targeting Cisco VPN accounts without Multi-Factor Authentication (MFA) in August, according to incident responder Aura.
On September 6, 2023, Cisco published a security alert claiming that the operators of the Akira ransomware had taken use of CVE-2023-20269, a zero-day vulnerability in the remote access VPN capability of two of their products: the Cisco Firepower Thread Defense (FTD) and Adaptive Security Appliance (ASA) software.
According to Cisco, bad actors can find legitimate credentials that could be used to create unauthorized remote access VPN sessions and, for victims running Cisco ASA Software Release 9.16 or earlier, create a clientless SSL VPN session by taking advantage of CVE-2023-20269.
A video analysis of the August 2023 Akira ransomware variant Megazord was just published by Sentinel One. Because it encrypts files with the "POWERRANGES" file extension, this variation seems to be referring to a Power Rangers formation. The ransom message, called "powerranges.txt," directs victims to use TOX messenger to contact the ransomware operator.
Security Recommendations
Organizations must take proactive steps to guard against emerging threats as skilled ransomware criminals create more complex families of malware. Organizations must strengthen their security posture as ransomware attacks change and take advantage of weaknesses to target companies globally, risking financial and reputational damage. The following security best practices can assist companies in defending against ransomware attacks on their vital mission data:
Audit & Inventory
- Make a data and asset inventory.
- Determine which software and devices are approved and unauthorized.
- Conduct an audit of the incident and event logs.
Configure & Monitor
- Take control of software and hardware setups.
- Only give access & administrative rights to employees when they are required.
- Keep an eye on services, protocols, and network ports.
- Turn on security settings on firewalls and other network infrastructure equipment.
- Create a software allowlist that only allows authorized apps to run.
Patch & Update
- Perform vulnerability assessments regularly.
- Apply operating system and application patches, or virtual patches.
- Upgrade programs and software to the most recent versions.
Protect & Recover
- Put backup, recovery, and data protection procedures in place.
- Activate Multi-Factor Authentication (MFA).
Secure & Defend
- Use sandbox analysis to prevent harmful emails from being sent.
- Install the most recent security solution versions on all system tiers, including the network, email, endpoint, etc.
- Recognize warning indicators of impending attacks.
- Employ cutting-edge detection technologies.
Train & Test
- Train and evaluate staff members on security abilities regularly.
- Carry out penetration tests and red team drills.
Organizations can protect potential points of entry into the system by using a multilayered strategy. Enterprises can also be protected by security systems that can identify suspicious activity and dangerous components.
- Trend Micro Vision One™: It offers multilayered protection as well as behavior recognition to prevent the ransomware from causing permanent harm to the system, which aids in the early blocking of dubious activity and tools.
- Trend Micro Cloud One™ Workload Security: It defends against known and unidentified threats that take advantage of security holes in systems.
- Trend Micro™ Deep Discovery™ Email Inspector: It successfully blocks dangerous emails using sophisticated analysis methods and customized sandboxing —including phishing emails, which can act as gateways for ransomware.
- Trend Micro Apex One™: It ensures endpoint protection by providing next-generation automated threat detection and response against sophisticated threats.
On the Whole
This blog post explores the growing danger of the Akira ransomware group, emphasizing how it uses Ransomware-as-a-Service (RaaS) distribution & double extortion. Akira uses strategies to target Canadian & US-based organizations and is affiliated with the Conti-ransomware gang.
This article emphasizes the importance for businesses to improve their cybersecurity defenses. Also, it covers the strategies Akira uses, the industries it impacted, and its current events, and offers security advice to minimize cyber threats.
Did you find this article helpful? If you want to read more of our unique articles, join our TTB Community on LinkedIn.