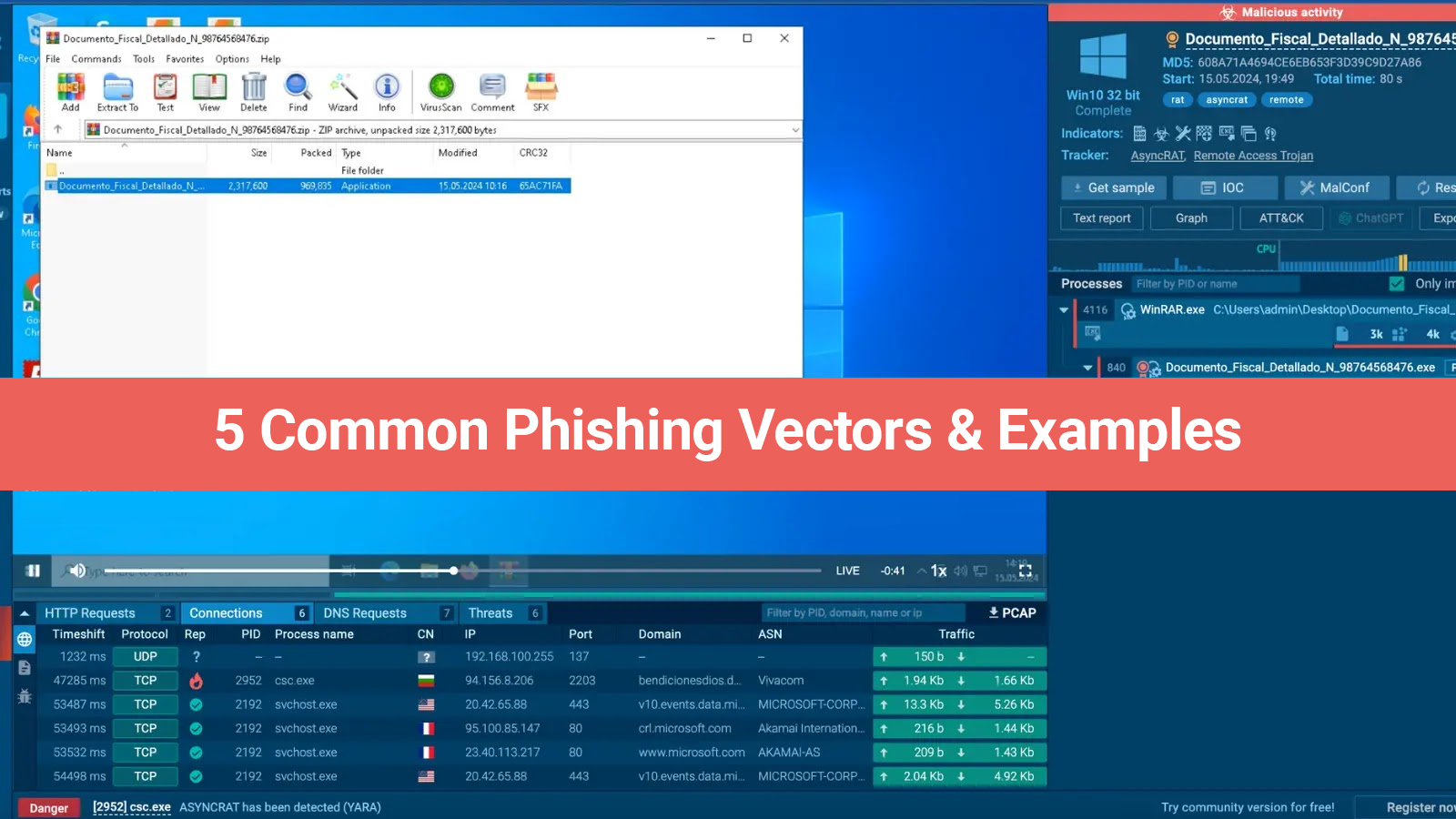
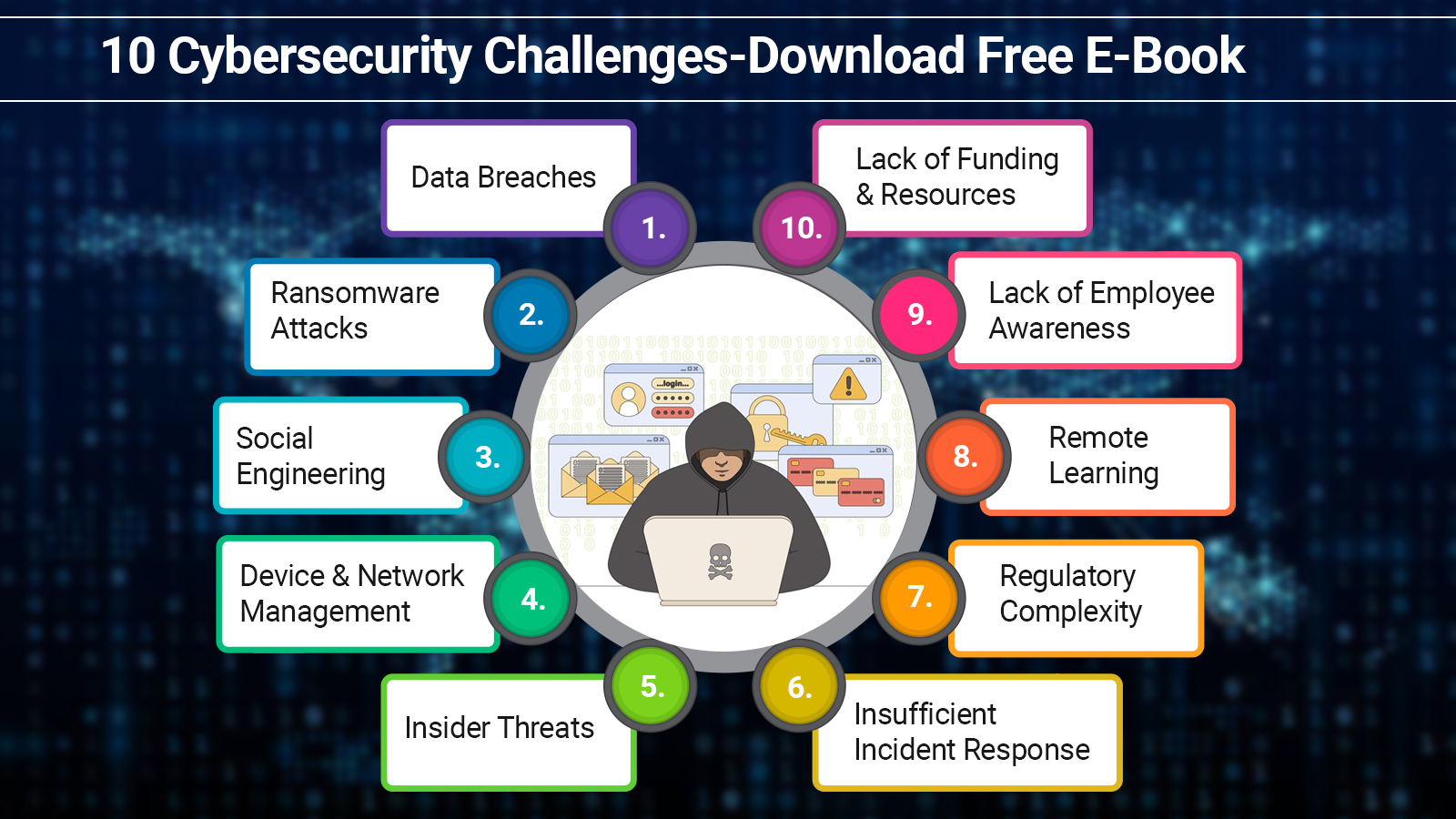
Whether to disrupt a nation, stop main commercial flows, or make significant economic improvements, cybercriminals usually examine for vulnerabilities that have not yet been found. The continuous growth of technology is a motivation for them to find unique spots to use. Thus, in a fast-evolving digital ecosystem, decision-makers in government, enterprise, academia, and the civil community need to predict and manage future cybersecurity challenges to stay ahead of the turn.
In Fall 2022, the Center for Long-Term Cybersecurity (CLTC), with help from the World Economic Forum’s Centre for Cybersecurity(spreads in a new tab), called decision-makers in management, enterprise, academia, and civil society for a string of workshops as a region of the initial stage of Cybersecurity Futures 2030, a strategy planning practice focused on examining how digital safety (extensively illustrated) could develop over the next five- to seven years.
The goal of these initial discussions was to shape an awareness of the “authorized end,” a baseline set of beliefs about what the future years will be like if current trends in cybersecurity resume on their present courses. Below are some of the key understandings, tensions, and trade-offs that occurred from the workshops, to help associations sufficiently ready for the chances, threats, and challenges that lie forward.
1. Cybersecurity progress, but wider access is needed
Public and personal investments in security technologies, as well as broader efforts to tackle cybercrime, defend critical infrastructure, and raise public awareness about cybersecurity, are likely to reap actual profits by 2030. Cybersecurity will be less about “protecting fortresses” than moving toward approval of continuous cyber threats, with a focus on strengthening resilience and ability for healing. As features of this trend, passwords could be nearly outdated by 2030, cybersecurity will be widely introduced in primary schools, and cryptocurrencies will be more virtually controlled. Still, while acquisitions in more protected systems and basic cyber hygiene will grow many above the “cyber poverty line,” improvement is possible to be unevenly spread across societies and topography.
2. Trust in the online world is deteriorating
The erosion of faith online is balanced to deepen and persist to damage offline connections and associations. Advancements in AI and device knowledge will make it increasingly hard to differentiate between humans and appliances online, potentially guiding many people to move their actions back offline and even revert to operating analog machines. In a planet of increasingly refined artificial media and AI-based cyberattacks, cybersecurity will become less about safeguarding confidentiality and more about defending the goodness and origin of data. Unfortunately, at the point when communities most need to arrive together to crack significant issues like temperature differences, doubt could lead to a retreat from provincial and international collaboration. We are required to work to bypass this product.
3. The dual effect of AI and machine learning innovations
There is both sanguinity and worry about the fast speed of scientific progress and retail adoption of AI and device education technologies. On the upside, we will see extensive invention in sectors such as pharmaceutical and vehicle, as well as modifications to cybersecurity. On the downside, AI will also lead to the invention of cybercrime, and machine-learning models could train themselves to conduct criminal or devious ends. There is a shortage of transparency on how governments, businesses, or residents will confirm that AI and other technology-based systems are made, deployed, and watched safely and ethically, and no obvious platform from which that direction will arrive.
4. Disadvantages and limited advantages of Internet splitting
The tendency toward “digital authority” and internet fragmentation will continue, as efforts toward internet interoperability and cross-border data transfers will contest with efforts by governments to show localized or local management over online slots. This may be a chance for regional residents to have more agents in determining digital protection, but we could also see an “absurd west” of disinformation, lookout, and additional strong cyberattacks originating from rogue states that have separated themselves from the international internet. The movement toward deglobalization could also lead to more prominent “regional pockets of fact,” with distinctions in data determined by geographic or other limitations, and governments could wield more control via technology.
5. A tug of war between regulatory investigations and the future of solitude
By 2030, we will understand whether earlier efforts at privacy legislation (such as Europe’s General Data Protection Regulation) are producing their policy goals, but it remains doubtful whether we will have enhanced strategies for handling confidential information by 2030 or will be living in a planet in which we have offered up on modern concepts of personal privacy.
6. Metaverse unreliability/variability
Players were divided between those who think that the metaverse (or metaverses) will not appear, and will be deemed a failed investigation by 2030 and those who think we need to accelerate policy creation to maintain the new privacy and safety problems that a fully recognized metaverse will pose. However, the most dystopian images of destiny that emerged from the workshops were established on a passive client (i.e., living in the metaverse to escape issues in the real globe). The remedy to this dystopia, and a key element of what the future holds, depends on our capacity to educate citizens to assume crucial thought.
7. Dominance and diverting power dynamics
In the workshops held in Europe, we attended concerns about a blurring of boundaries between governments and personal companies (for example, a few players assumed a future in which the biggest tech businesses hold seats on the UN Security Council). From US-based players, we heard more worries about a trend toward digital dominance, the protection problems enterprises face in managing increasingly divergent regulatory needs around the globe, and the absence of a practical human rights framework for resolving adherence trade-offs. Most agreed that the public sector will play an essential role as both consumer and investor in technology and in creating barriers in how cybersecurity plays out. Security practitioners must take a holistic view of the advance of digital technologies to remain ahead of the turn. Those who start now to look toward this complex new future will have the benefit.
Did you find this article interesting? Join our TTB Community on LinkedIn for more intriguing articles & updates.