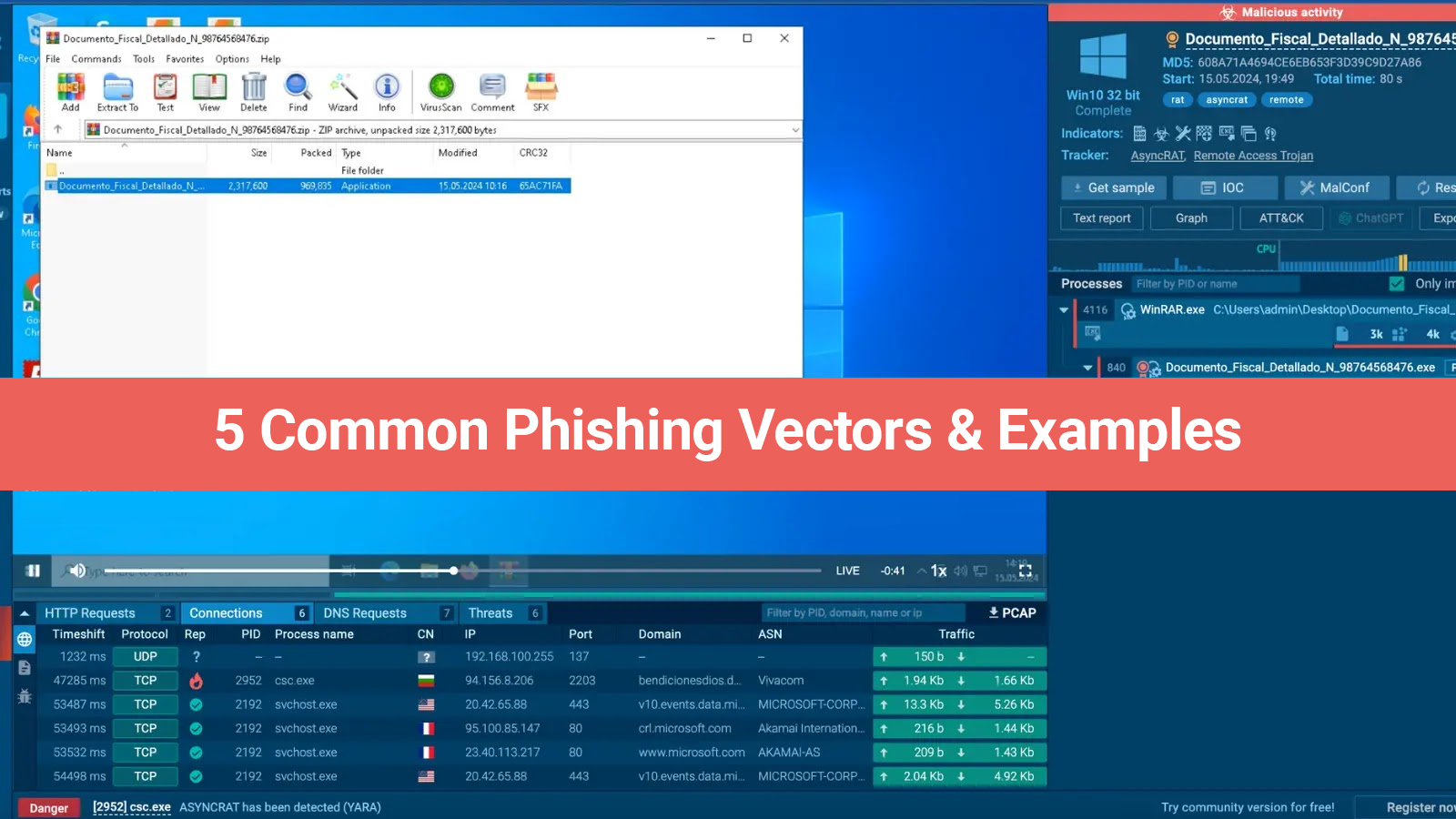
A refined malware movement has been recognized, especially targeting Windows and Microsoft Office users via smashed software. This nasty procedure influences software crashes, often desired behind unauthorized activation of famous software, to broadcast Remote Access Trojans (RATs) and coin miners, posing substantial hazards to individual and corporate cybersecurity.
Continual Menaces Employing Ingenious Tactics
Once established on a victim’s method, the malware operates advanced procedures to guarantee its continuation. It cleverly reports orders within the assignment scheduler, which authorizes it to preserve a foothold on the infected system.
According to the current news from Broadcom, this perseverance allows the ongoing structure of unique malware payloads, even after initial reduction attempts, creating a specifically headstrong and risky hazard. Symantec, the highest cybersecurity business, has recognized several hands of settlement associated with this movement, including adaptive-based, carbon black-based, file-based, machine learning-based, and web-based indicators. These hands help catch and choke the negative actions triggered by this malware.
The malware variants determined in this movement, such as ACM.Ps-Http!g2, ACM.Ps-Masq!g1, and ACM.Ps-Reg!g1, are virtually witnessed and barred by existing procedures within VMware Carbon Black outcomes. VMware Carbon Black suggests guidelines that, at a minimum, intercept all types of malware from managing, including general malware, suspicious malware, and potentially undesirable programs (PUPs). This system, connected with a pause in implementation for cloud scans, maximizes the advantages derived from VMware Carbon Black Cloud’s reputation service.
Detection Methods: File-Based and Machine Learning Approaches
The movement also uses downloader malware and Trojan horses, recognized as ISB. Downloader!gen221 and Trojan.Gen.MBT, respectively. These hazards are part of a more expansive plan that uses advanced machine learning-based detection mechanisms, such as Heur.AdvML.A!300 and Heur.AdvML.B sequence to recognize and balance probable hazards before they can force damage.
The operation’s web-based segment concerns using marked domains and IP addresses concealed under safety classifications in all WebPulse-enabled consequences. This all-around range guarantees that attempt to express with authority and control servers or download added nasty payloads are connected, rescuing users from the movement’s distance.
This malware movement highlights the hazards associated with downloading and using smashed software. Above the legal and honorable importance, such software reveals users to influential cybersecurity perils. Users are encouraged to download software only from authorized merchandiser websites and to utilize vital cybersecurity standards, including reputed antivirus and antimalware resolutions, to defend against such refined hazards.