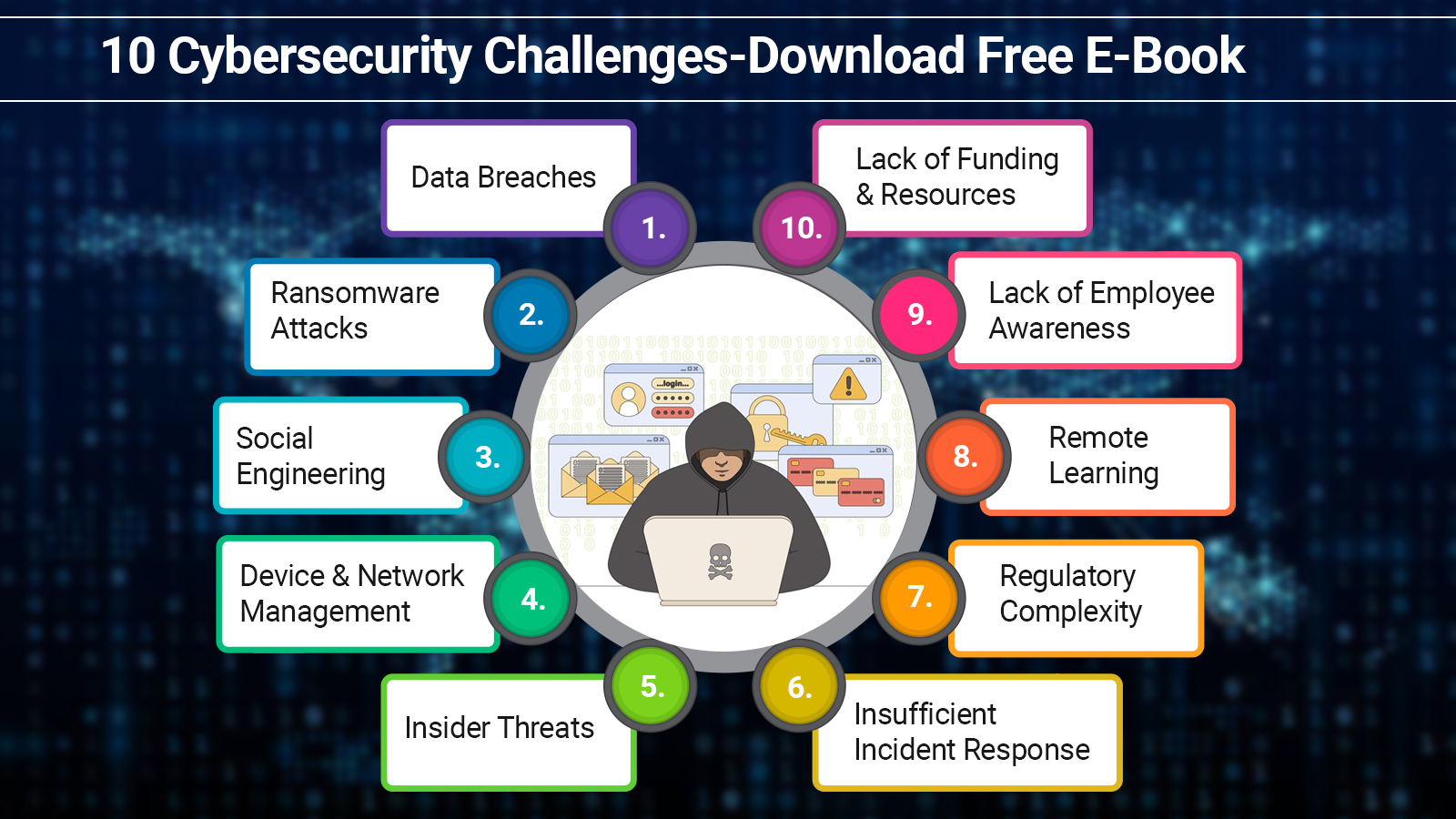
Students aren’t alone in having their talents tested in K-12 schools. Education-sector IT groups face mounting stress to deliver cost-effective cybersecurity as hazard actors increasingly target schools as “effortless targets” with ample entrance to susceptible information. The 10 protection challenges commonly undergone by K-12 schools are hidden beneath. Explanations for each challenge are described in more depth by Cynet’s new direction for free, “Top 10 Cybersecurity Challenges Fronted by K-12 Associations.”
In expansion to the sector's most promising methods, the advice is founded on Cynet’s victorious partnerships with schools like Goshen Community Schools in the US or Wigmore School Academy Trust in the UK, as well as high-ed heads like Grambling State University. Through a suitable assortment of platforms, individuals, and operations, IT leaders can overcome the following barriers to protected systems for student victory:
- Mitigating Data Breaches
Challenge: 87% of scholarly institutions have been breached by a cyberattack. The increased rate of settlement arises from several aspects.
- Schools store extended pieces of privately identifiable data (PII), including student documents, economic data, and personnel details, making them appealing targets for cybercriminals.
- Schools usually work with restricted budgets and resources, due to obsolete IT infrastructure and inadequate cybersecurity standards.
- Faculty, staff, and students lack the practicum to spot and convey cyberattacks.
- As schools become increasingly interconnected through technology adoption, vulnerability to dangers and exposures grows.
Explanation: Holistic threat removal requires a broad practice containing technological management, continuous practicum, and acquisition of resources to safeguard susceptible data.
2. Preventing Ransomware Incidents
Challenge: 80% of K-12 providers were hit by a ransomware attack in 2023 — costing $1.42 million per happening to remediate on moderate. In expansion to the economic harm, ransomware attacks cost schools three days to three weeks of lost understanding time during healing.
Explanation: Schools can decrease the hazard of ransomware incursions by deploying backup and tragedy recovery resolutions, updating their IT infrastructure, and executing vital protection authorities. Incident reaction methods and training are also essential to fortunate healing, underestimating the impact on students.
3. Combatting Social Engineering Tactics
Challenge: About 30% of education-sector workers have lost to phishing fraud. In many such circumstances, cybercriminals mock school managers, IT staff, or other trusted commodities to mislead “coworkers” into revealing susceptible details or relating to negative connections.
Explanation: There are specialized standards to mitigate social engineering threats in expansion to normal understanding training. Email filtering and authentication protocols can prevent phishing emails from getting recipients’ inboxes and intercept negative affections. Territory filtering means stopping users from linking to malicious zones.
4. Effective Device and Network Management
Challenge: With the addition of mobile gadgets, laptops, tablets, and IoT devices, IT teams in schooling must address increasingly complicated network backgrounds, facilitating dedicated connectivity and tickets to educational resources — without compromising safety. Compounding the sophistication, more schools are embracing BYOD (bring your device) guidelines, adding a superabundance of individual devices to the mixture.
Explanation: Schools must execute vital endpoint protection actions to rescue both school-issued and individual devices against malware, unauthorized access, and data violations. This includes deploying antivirus software, implementing robust password guidelines, and enforcing endpoint detection and reaction (EDR) resolutions.
5. Inadequate Funding and Resources
Challenge: Funding threatens big in the senses of K-12 technology executives. They must balance contending preferences for budget for an exhibition of technology industries, and periodically cybersecurity feels the reduction. Fixed assets can guide to ancient IT infrastructure, insufficient protection standards, and a deficiency of trustworthy cybersecurity personnel. Heritage systems may lack fundamental safety features and updates, making them more sensitive to exploitation.
Explanation: Current incorporated cybersecurity platforms, such as Cynet’s All-in-One Cybersecurity Platform, shield numerous disciplines. Consolidated abilities are far more reasonable, not to mention more straightforward to work, than buying numerous standalone resolutions.
6. Addressing Employee Awareness Gaps
Challenge: Cybersecurity attention in K-12 schools is usually lacking supply. That students are not to be depended upon as standards of cybersecurity's most useful approach nearly goes without speaking. However, trainers and staff may not be acquainted with the techniques cyber assailants use to penetrate networks, steal confidential and institutional data, or disrupt educational procedures.
Explanation: Schools should incorporate continuous, age-appropriate cybersecurity education into curriculums and experienced expansion timetables. Exercises and simulations should also be executed regularly to train staff and students to react to a cyber happening.
7. Remote Learning Solutions
Challenge: Schools must guarantee that students, faculty, and staff can securely access online education media and resources from distant places without compromising acute data.
Explanation: Small understanding hazards can be managed via aggressive, layered cybersecurity standards, including powerful authentication agents, encrypted data communication, and constant monitoring for unauthorized entrance or questionable manners.
8. Navigating Regulatory Complexity
Challenge: K-12 schools are subject to a variety of data privacy measures, such as FERPA in the United States, that define stringent information security standards, periodic audits, and necessities for staff to comprehend their duties under these laws. Non-compliance can result in significant fines, not to mention harm to the institution’s standing.
Explanation: Periodic checks and updates to information security guidelines and protocols must adjust to changes in the law, as well as developing cyber dangers. Third-party help can supply schools with technical expertise. Log supply and control also helps to assess and help regulatory compliance.
9. Managing Insider Threats
Challenge: Students, faculty, staff, or contractors may misapply their user rights — knowingly or by blunder — to achieve unauthorized access to acute data and systems.
This can lead to information exfiltration, for example, where people swipe or reveal confidential details for private profit or evil intentions. Even without malintent, insiders may inadvertently disclose susceptible data through negligent handling of data.
Explanation: IT teams in instruction should enforce access management to restrict confidential credentials to necessary personnel, observe user action for symptoms of questionable manners, and implement protection guidelines and practices to control data mishandling.
10. Inadequate Incident Response Preparedness
Challenge: Many schools are ill-prepared to rapidly catch and hold a cyberattack. Their lack of specific response planning can result in pricier healing and prolonged disturbance to academic exercises.
Explanation: IT teams must cooperate with school stakeholders to specify exact techniques and protocols for reply if a safety happening occurs. Strategies should clarify functions and duties for incident reaction team associates, select contact media for writing and escalating incidents, and abstract procedures for remediation.
Similarly, by proactively performing threat reviews and susceptibility scans, schools can determine possible flaws in their plans and prioritize resources for relief measures.
Conclusion
K-12 administrators cannot afford to let managerial conditions compromise protections for students. A way ahead is supplied by the most promising techniques in the manual, “Top 10 Cybersecurity Challenges Faced by K-12 Institutions.”
To provide strong benefits to IT teams in education, Cynet’s All-in-One Platform offers strong benefits to IT teams in education by unifying a full suite of cybersecurity abilities on a single, easy medium that’s supported by 24/7 access to on-demand help. Sign up for a one-on-one demo with a Cynet professional to see how it could benefit your team and improve cybersecurity for students, teachers, parents, and staff.
Did you find this article interesting? Join our TTB Community on LinkedIn for more intriguing articles & updates.