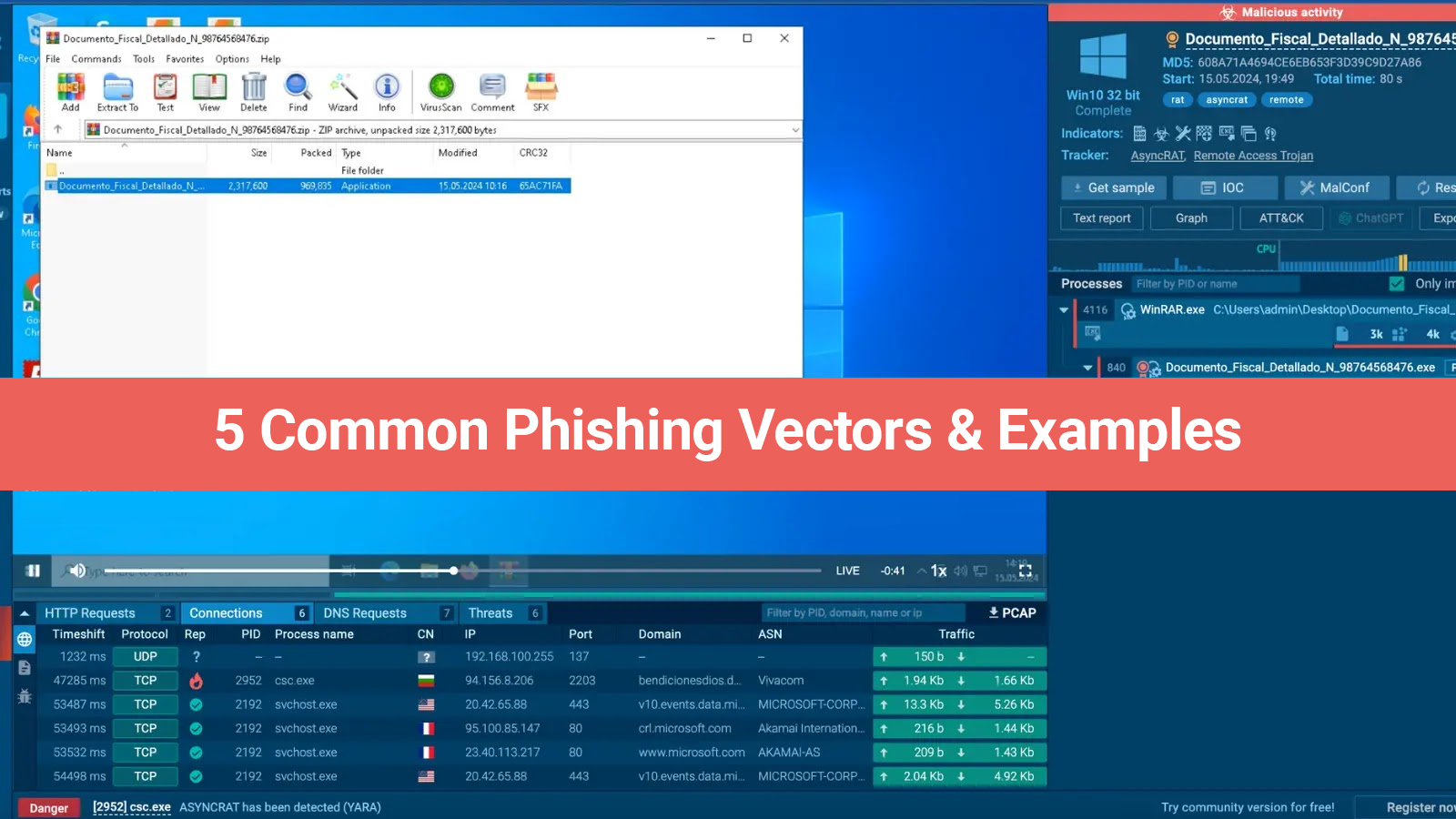
The latest perils, exposures, data violations, and defensive countermeasures are hidden in the weekly cybersecurity news overview. To enhance your security stance and guards, you must have up-to-date details on two key things occurring cyber dangers and attack vectors. Active hazards may be overwhelmed by maintaining situational caution across this landscape of a rapidly changing nature so that your investments are shielded at all terms.
Cyber Attacks
Critical infrastructure is being attacked by Russian APT hackers
The report concerns the Russian APT cyberpunks who are entangled in targeting crucial infrastructure and utilizing other simple software installations to put their malware into operation.
Among these, ShadowPad RAT has been linked with them, whereas they utilize a broad spectrum of tactics such as many backdoors at the exact moment for making identical contact media with impure systems. These include well-researched phishing emails, domain controller hijacking, and embezzling secret data that will be reserved in servers hosted from different regions of the globe. Robbed data is forwarded from C&C servers utilized in these attacks to direct two servers found in China.
An attack on Foxit PDF Reader users has been reported by hackers
A structure defect in the method it alerts users about its safety has been discovered by investigators, and a PDF exploit targeting Foxit PDF Reader users is now known. Potentially, an assailant can make a nasty code to be managed by tricking users with the default “OK” options for safety warnings. Shifting from standard protection tools, this spot allows malware writers to fool users into clicking “OK” without any choice for the danger that will result.
This bug permits cyberpunks to download and execute malware on victims’ devices once they entice them into staying at Websites beneath their authority. Rather than utilizing traditional techniques to tackle attacks, social engineering is utilized to make this exploit less noticeable. Other dangerous preferences have witnessed the exposure vigorously used in real-world attacks.
Weaponized WinSCP & PuTTY Delivers Ransomware
Assailants established a movement in early March 2024 broadcasting trojanized installers for WinSCP and PuTTY, which directed to downloads including malware. The malware used a renamed pythonw.exe that loaded a nasty DLL, which side-loaded an honest DLL and infiltrated a Sliver beacon using nostalgic DLL injection.
The attackers then selected the industry, downloaded more payloads, attempted to steal data, and deployed ransomware, showing TTPs similar to those operated by BlackCat/ALPHV in history. The ad for PuTTY download shifted users to a typo-squatted territory hosting a negative download connection, and clicking the link triggered a chain of redirects, eventually downloading a malware-laced ZIP archive hidden as a PuTTY installer from a compromised WordPress environment.
400k Linux Servers Hacked
Cryptocurrency robberies and other economic crimes are being taken out by a massive botnet comprising over 400,000 hacked Linux servers, according to a new study from ESET cyber safety professionals. Ebury illegal crowd is liable for managing this botnet that has been in process since 2009 with numerous propagation techniques including hijacking hosting providers’ infrastructure as well as ARP spoofing attacks. The network’s size has ballooned and it still had more than 100,000 infected servers till the end of 2023.
Apart from classic spamming and executing traffic to other sites, this botnet also robs economic data and an abundance of cryptocurrencies on infected devices. The latest version of Ebury malware embarked in late 2023, updated digit 1.8 enhanced its rootkits to be more challenging to see, added a new field generation algorithm, and made concealing any data better.
Threats
New Linux Backdoor
One of the recently acquired Linux backdoors is determined which was dubbed “Linux.Gomir.” It was made by the North Korean cyberpunk batch Springtail and has been repeatedly attacking users via installation packages. This backdoor acts as GoBear’s replica and conveys with its C&C server over HTTP POST where it first hashes the hostname and username before transmitting a disease ID.
It uses a special form of encryption to analyze controls, this displays the group’s capability to attack media in various backgrounds. A second alert discovers an evil code in XZ Utils versions 5.6.0 and 5.6.1 that presents a backdoor via SSH into individual Linux allocations, concerning servers receiving incoming SSH links.
Users should demote to natural versions and check for center signs on their systems that are impacted by this exposure. The XZ Utils backdoor, located in the open-source library XZ Utils, permits small code execution and was buried into the program by one of its designers who had been engaged in creating it for two years before being elevated to the maintainer’s assignment. The latest releases of XZ Utils are vulnerable to this backdoor, indicating that downgrading compromised versions is essential when controlling such attacks.
ViperSoftX Malware
A new auditory keyboard side-channel attack has been discovered by cyber security investigators, which can be used by cyberpunks to rob vital data by grabbing the sounds of keystrokes with the help of microphones. This episode consists of waveform research that qualifies for removing such details as timing and power. At this moment, statistical research, device learning, and signal processing come into play.
The writers propose a way in which keystroke audio is arrested, a statistical measure is introduced for projection, and an English dictionary enhances outcomes for expecting terms even if there is noise. The study aims to make it achievable to recognize keystrokes without depending on conditions in the environment exactly. It highlights how critical it is to register accurate keyboard voices to catch them efficiently.
QakBot Malware
The report consults the finding of a zero-day exposure in Windows OS, especially the Windows Desktop Window Manager (DWM) openness, specified as CVE-2024-30051. This vulnerability permits assaulters to escalate requests. The record including details about this exploit was uploaded to VirusTotal on April 1, 2024.
After documenting the results to Microsoft, a patch was released on May 14, 2024. The exploit has been marked in attacks affecting QakBot and other malware, specifying numerous hazard actors have access to it.
New Social Engineering Attack
Cybersecurity critics at Rapid7 have recognized a new social engineering attack that delivers the Black Basta ransomware. The attack begins with a surge of apparently innocuous newsletter enrollment verification spam emails that avoid email safety. Assaulters then make phone calls acting to be IT sustain to convince users to permit small access via devices like AnyDesk or Quick Assist.
SugarGh0st RAT
The attack begins with a surge of apparently innocuous newsletter enrollment verification spam emails that avoid email safety. Assaulters then make phone calls acting to be IT sustain to convince users to permit small access via devices like AnyDesk or Quick Assist. There is a new movement targeting AI research organizations in the United States by use of SugarGh0st Remote Access Trojan (RAT). For example, UNK_SweetSpecter has been discovered responsible for this process and it has cruelly impacted multiple companies, national agencies, and colleges.
Darkgate Malware
Windows devices are targeted using hostile devotions such as XLSX, HTML, or PDF files in phishing emails. The malware can clone itself and take custody of impacted funds with hazards such as data loss, fraud, and compromising susceptible data. QuickBooks invoices which are used to hide phishing emails from this movement make users download JAR files including blurred AutoIt scripts that correspond with small servers.
Data Breach
Nissan Data Breach
Nissan Oceania has demonstrated that in December 2023, approximately 100,000 individuals, including clients and workers were impacted by the information violation. The breach resulted from a third party without consent accessing regional IT servers. The Akira ransomware trust however asserts they did it and revealed embezzled details.
Hackers Abusing to GitHub
There have been examples of Russian-speaking danger actors from the Commonwealth of Independent States (CIS) utilizing GitHub as a medium to host opposing infrastructure and spread different states of malware. They create miniature GitHub profiles and holds that imitate recognized software programs, fooling individuals into downloading pirated versions packed with malware such as the Atomic macOS Thief.
Vulnerabilities
New Google Chrome Zero-day
A proof-of-concept (PoC) exploit has been publicly released for a small code implementation (RCE) zero-day exposure in D-Link EXO AX4800 (DIR-X4860) routers. The vulnerability permits unauthenticated distant assailants to acquire high concessions and direct orders as the basis by incorporating an authentication bypass with command injection.
FortiOS & FortiProxy SSL-VPN Flaw
Fortinet witnessed a significant vulnerability named FG-IR-23-225 in FortiOS SSL-VPN and FortiProxy SSL-VPN, allowing hazard actors to bypass safety authorities that may have been set by the companies on the systems and spoof IP addresses via prepared packets. It can affect a broad spectrum of interpretations of FortiOS and FortiProxy and thus can result in a possible violation of unauthorized access to resources on the secure network.
30+ Tesla Cars Hacked
In a cybersecurity battle, cyberpunks won $200,000 by taking advantage of defects in the modem and infotainment system of a Tesla. The Zero Day Initiative’s event is suggested to witness problems in-car electronics. To hack into this Tesla vehicle, Synacktiv, the endearing team utilized some bug chains and thus earned a sum of funds that counted up to $450,000.
Hackers Exploiting Microsoft’s Quick Assist
Hazard actors are exploiting Microsoft’s QuickAssist small access device to disseminate ransomware in the image of social engineering attacks. The cyberpunks from Storm-1811 have been seen to take the power of computers and propagate Qakbot, Cobalt Strike, and yet Black Basta ransomware.
Other news
Apple Has Terminated 370 Million+ Developer & Customer Accounts
Apple just removed more than 370 million designer and client accounts in 2023 to fight fake and guarantee a safe medium for users and designers. This action is part of Apple’s continued actions to improve antifraud standards and keep the virtue of the App Store. The organization’s strict fake deterrence investigation directed the omission of millions of accounts and the refusal of scheming designer enrollments, showing Apple’s dedication to rescuing its ecosystem.
Tor Browser 13.0.15 Released
Tor Browser 13.0.15 has been released, which features important safety updates and fault fixes. It is the Tor network’s unknown door to Firefox. It routes traffic via a network of volunteer relays to conceal a user’s area and use it from anyone conducting network management or traffic research. The browser is known for Windows, macOS, Linux, and Android and is localized in 37 speeches. Users can then customize their privacy and protection settings consequently among three potential statuses of security like normal, more unassailable, or secure.
Did you find this article interesting? Join our TTB Community on LinkedIn for more intriguing articles & updates.