Information is ultimately what allows cybersecurity professionals to react to threats proactively & effectively. Using threat intelligence platforms is one of the most effective ways to gather it. Their provision of threat context and enrichment facilitates the transition of analysts from reactive defense to proactive threat hunting by giving them the confidence to make well-informed conclusions.
Threat Intelligence Platforms: What Are They?
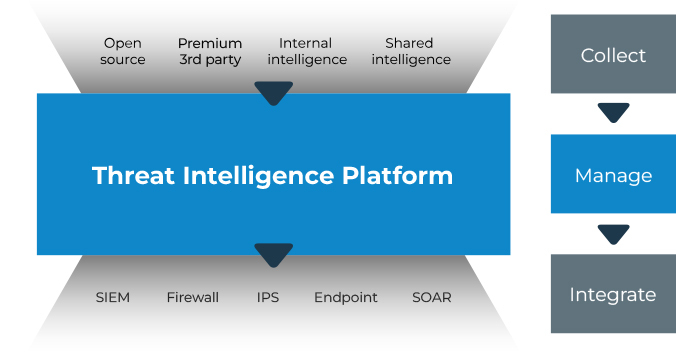
Through partnerships with industry organizations and security experts, a Threat Intelligence Platform (TIP) is a searchable repository of threat intelligence that provides real-time updates on new and existing malware, vulnerabilities, and attacker strategies. This data is derived from multiple sources, such as sandboxes, Open-Source Intelligence (OSINT), threat intelligence streams, etc.
Network indicators (IP addresses, domain names, URLs) and malware data (file hashes and names, domains, tactics, techniques, and procedures) are among the information that can be found on TIPs.
The searchable elements for Threat Intelligence Platforms (TIPs) that use malware analysis sandbox data go beyond simple Indicators of Compromise (IOCs) and include specific system data including command lines, registry activity, and active processes.
Utilize the ANY.RUN Sandbox's Threat Intelligence Lookup Capability
ANY.RUN is a malware analysis sandbox used by over 400,000 experts globally. Participate in the community to gather comprehensive reports on the behavior of the biggest threats and to perform in-depth investigations into them.
Let me demonstrate how to use a TIP by assuming that you receive an alert about an unusual URL. Using a TIP, you may quickly run a search query to get dangerous information about this URL, such as the threat level, malware that is linked with it, and even sample data. With this whole view, you may make informed decisions about escalation, blocking, or further investigation.
The Importance of Threat Intelligence Databases
1. Putting Security Alerts in Perspective for Well-informed Prioritization
Threat Intelligence Platforms (TIPs) enhance the value of threat warnings by providing additional context. By adding dangerous signatures and artifacts associated with threats to alerts, TIPs help analysts focus their attention and prioritize the most critical issues. Through the evaluation of a threat's malicious activities and potential effects, researchers can optimize the time and resources allocated to their research.
2. Using Proactive Threat Hunting to Detect and Mitigate Emergencies Early
Adapting to changing cyber threats requires a shift in security from reactive to proactive. By giving analysts the means to engage in proactive threat hunting, TIPs enable them to do more than simply respond to alarms.
For example, analysts can query various data sources using particular indications, trends, and behaviors to discover potential dangers thanks to TIPs' extensive search capabilities.
In addition, new information regarding vulnerabilities, attacker tactics, methods, and procedures (TTPs), and emerging threats is included in TIPs, which enables analysts to remain ahead of and prepare for possible assaults.
3. Expanding the View of the Threat Landscape to Make Well-Informed Security Decisions
A thorough awareness of the changing threat landscape is essential for making wise security decisions. As a central hub, TIPs compile information from multiple sources. As a result, analysts can understand the threat landscape holistically and make linkages and patterns between seemingly unrelated occurrences.
Utilizing Threat Intelligence Lookup for Advanced Search
Now let's examine TIPs' functions and practical applications. A TIP called Threat Intelligence Lookup (TI Lookup) utilizes data taken from the massive database of millions of interactive malware analysis sessions (tasks) in the ANY.RUN sandbox. Consequently, it enables you to create complex inquiries utilizing more than 30 fields—including registry paths and Suricata rules—instead of only performing straightforward keyword searches. These are a few of them:
1. Combined & Wildcards Requests
A uniform vocabulary for characterizing attacker tactics, methods, and procedures (TTPs) is offered by the MITRE ATT&CK framework. By allowing you to look for certain tactics or combinations of techniques in your threat intelligence data, TI Lookup maximizes the capability of MITRE ATT&CK.
Let us make the following inquiry: THEFT: "^T108" AND THEFT: "remcos"
The site offers one hundred distinct Remco samples in addition to associated incidents involving the application of MITRE methodologies beginning with "T108".
By visiting the ANY.RUN sandbox, we can examine each of these samples in further depth. Here, we can examine the processes that were started during the malware's execution, see network and registry activities, and gather insightful intelligence reports.
2. Looking for Particular Registry Keys
You can use TI Lookup to look for certain registry keys, including ones that include backslashes in them. But it's crucial to double the backslash character in your query to avoid it.
Example:
RegistryKey: "HKEY_LOCAL_MACHINESoftwareMicrosoftWindowsCurrentVersionRun"
This request looks for any instances of processes or applications that are set up to launch automatically. More than 400 distinct events are found by the platform that fit the search parameters.
3. Examining File Hashes
TI Lookup provides extensive search functionality with many file hashes, such as SHA256, SHA1, and MD5. This enables you to immediately recognize possible risks by using malicious file signatures that are known to exist.
Example:
SHA-256:”7c2cf95543435f55cf814477874ba460fc6efc39438c15fb5bf49ffeb4142c2e”
This query looks for all instances on the platform where the file with the particular SHA256 hash has been examined. The outcome demonstrates that this hash is part of a file connected to the RisePro virus.
4. Focusing on Particular Process Paths
You can look for instances when a certain process route has been noticed, much like with registry keys. To escape your query, don't forget to double the backslash character inside it.
Example: ImagePath:"C:WindowsMicrosoft.NETFramework64v4.0.30319csc.exe”
This query looks for instances in which the C# compiler is running. Thirteen tasks are returned by the platform along with files and events associated with the query.
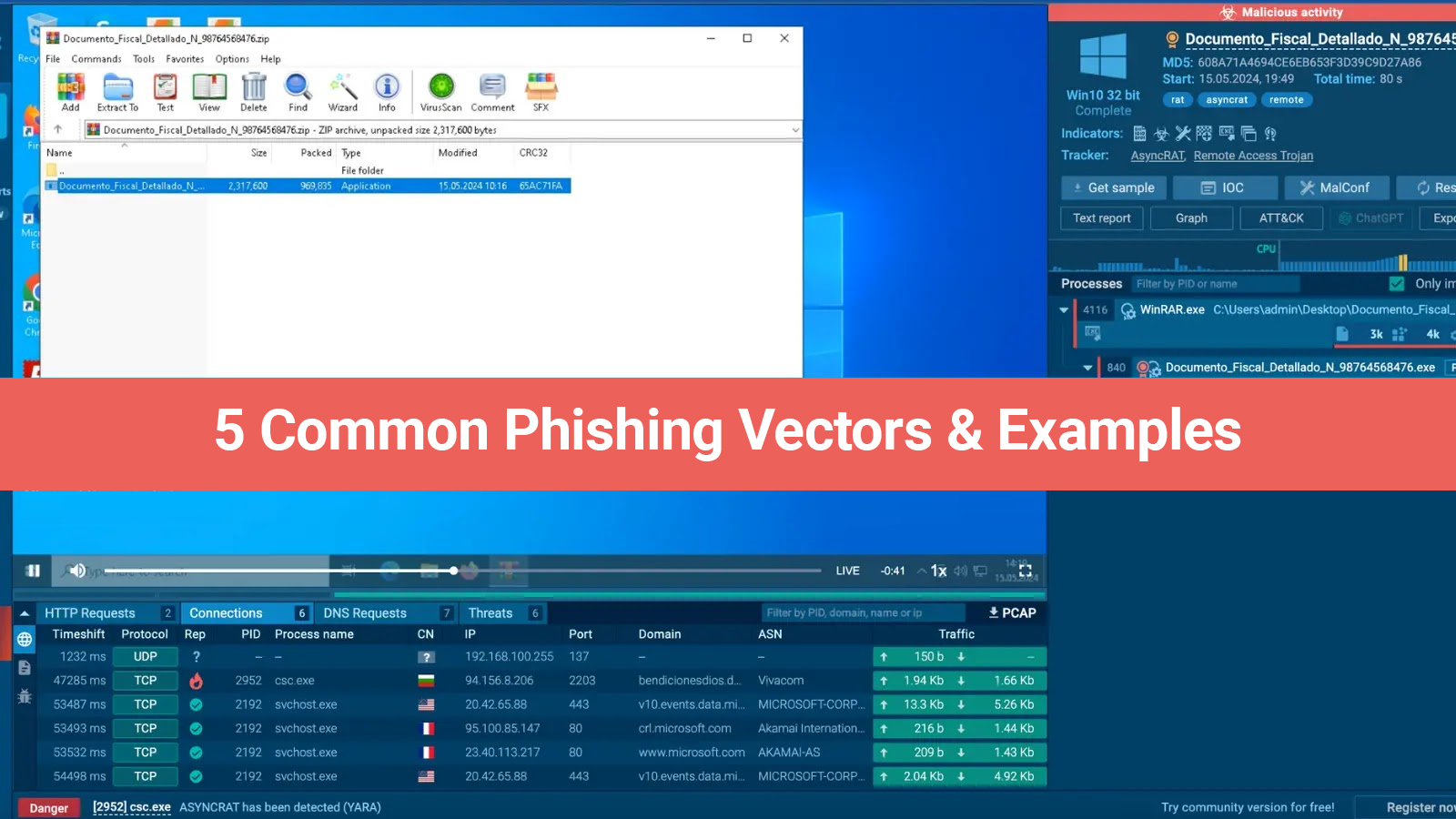
5. Making Use of IP Addresses
The last option is to include IP addresses in your search terms. This enables you to look at particular endpoints or find possible geographic patterns linked to risks.
The screenshot above's query looks for all instances involving the specified IP address. It is promptly recognized as malicious by the platform, which also offers links to the Asyncrat virus and pertinent URLs, files, tasks, and events.
Bringing It To A Conclusion
In the field of cybersecurity, threat intelligence platforms, or TIPs, are vital tools for conducting prompt and thorough threat investigations. Tip compiled lists of the most recent malware, vulnerability, and attack tactics, giving analysts the background knowledge they need to move from reactive threat hunting to proactive threat hunting.
Through contextualizing security alerts, TIPs help analysts prioritize, discover threats early, and see the whole threat environment. They achieve this by making use of robust search tools and broad data sources.