While many Americans celebrated Thanksgiving in 2023, hospitals around the country were acting somewhat differently. There were malfunctions in the systems. An ambulance was rerouted. Care was compromised. A ransomware attack crippled hospitals across three states, and at that point the real-world effects were apparent—actual patient care was disrupted in addition to computer networks.
More than ever, cybercriminals are taking advantage of smaller healthcare businesses in an attempt to profit handsomely. Although it might be comforting to think that there was formerly a code of behavior for thieves, if such a thing ever existed, it has long since been disregarded.
These days, sophisticated hacker groups are more than willing to target healthcare providers such as nursing homes and clinics with cyberattacks. Unfortunately, fraudsters can now easily steal sensitive data from small- to mid-sized healthcare institutions, demand large ransoms, and, worst of all, jeopardize vital patient care.
Phishing & Ransomware Attacks are Proliferating at an Unhealthy Pace
When working in the medical field, everything you do matters. That's why it's so alarming how frequently attacks on healthcare organizations occur these days. The U.S. Department of Health and Human Services (HHS) reports that the number of significant breaches increased by 93% between 2018 and 2022. Ransomware-related breaches have increased by 278% within that same time frame.
Ransomware not only threatens your finances but also jeopardizes the security of your patients. You're momentarily locked out of your systems, at best. At worst, there is a major lapse in patient care. This is particularly concerning if you serve smaller areas where the primary and secondary sources of crucial care for the locals are your clinic, cancer center, or doctor's office.
Of course, your patients should come first, but you also need to think about the money involved. According to the HIPAA Journal, the healthcare sector's average ransomware payment in 2021 was $197,000. And that is a 33% rise over the previous year!
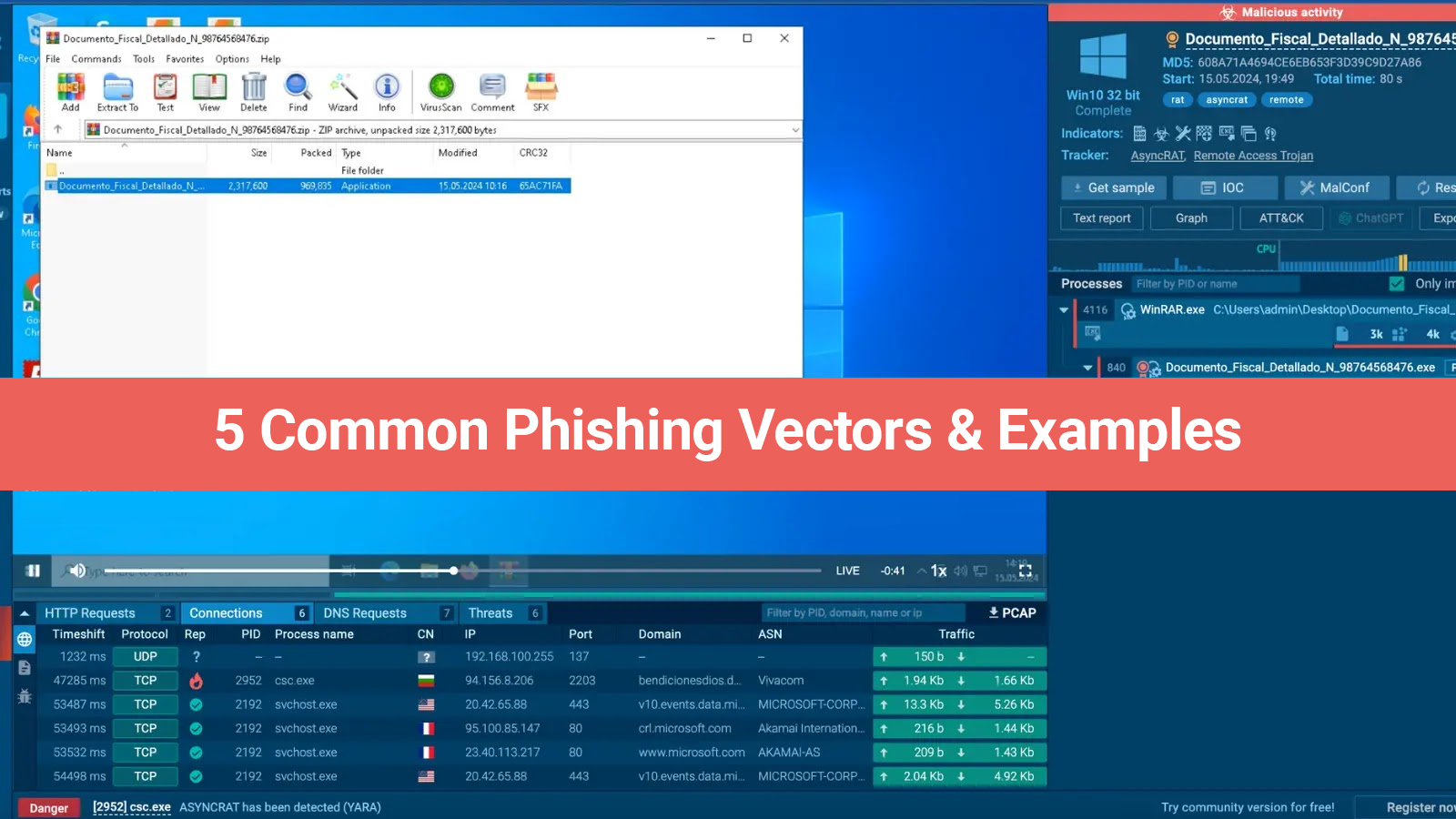
These days, phishing—fraudulent emails purporting to be reputable sources and intended to obtain personal information—is the most widely used attack technique. According to The HIPAA Journal, phishing scams account for over 90% of cyberattacks against healthcare institutions. This implies that a single, thoughtless click on an email could have disastrous effects on your patients, employees, and business.
In addition to the possible financial strain that cybercriminals may cause, Health Insurance Portability and Accountability Act (HIPAA) fines may be severely crippling. You may face fines of tens of thousands of dollars for each infraction if you allow yourself to be a victim of data breaches. As an illustration, the HHS's Office for Civil Rights recently settled the first-ever hacking case involving a medical group in Louisiana by paying an astounding $480,000 fine. All of this was the outcome of a straightforward phishing scheme in which a hacker obtained access to the medical group's Microsoft 365 environment, which serves as the repository for the Protected Health Information (PHI) of its patients.
Less Resources and More Endpoints Make Healthcare Targets Easier
Put simply, human skill and cutting-edge technology are both necessary for effective cybersecurity. However, Huntress found that more than 60% of respondents did not have any specialized cybersecurity professionals on staff, according to the report The State of Cybersecurity for Mid-Sized Businesses in 2023. This is because a lot of Small & Medium-Sized Businesses (SMBs) face limitations and struggle to achieve even one of these essential elements. SMBs, both in and outside of the healthcare industry, have had to cut costs due to a range of economic circumstances, which includes giving up much-needed investments in cybersecurity personnel and technologies.
The Healthcare Information and Management Systems Society (HIMSS) reports that the average IT budget for healthcare businesses is less than 6% of the total amount allocated to cybersecurity. Completing internal tasks with suitable applicants has become increasingly difficult due to the severe scarcity of cybersecurity talent. Additionally, the finest applicants are demanding top-level salaries, which are occasionally out of reach for smaller healthcare firms due to the scarcity of top talent.
Aging technology is also not a beneficial factor. Older hardware and operating systems have become convenient entry points for online thieves. Because their defenses are weaker, smaller healthcare companies are therefore prime targets. Your IT staff might need more resources or personnel to handle the ever-evolving cyber risks, or they can be overworked.
The fact that there are more endpoints than ever before to secure only adds to the mayhem. Over the last ten years, telehealth and remote work have increased dramatically—most notably during COVID-19. The good news is that healthcare professionals, including you, may now supervise and support patients from a distance while they remain comfortable in their own homes. However, this caliber of care necessitates additional data access points, particularly through tablets, laptops, and mobile devices. On the other hand, this also implies that there are more attack vectors available for dishonest people to obtain your information.
The Threat Environment is Changing, Getting Worse
The increasing organization of cybercriminals is one factor contributing to the rise in risks. And even more callous. It's not the naughty little kid lurking under a black hoodie in a pitch-black cellar, crouched over a monitor. These are highly skilled criminal organizations capable of pulling out meticulously planned heists. Think of Ocean's Eleven, although far less stylish and regrettable.
US intelligence has even discovered hacker organizations connected to adversarial countries. These state-sponsored cybercriminals, sometimes referred to as Advanced Persistent Threats (APTs), possess the ability to cripple a wide range of infrastructure, including electric grids, natural gas pipelines, and water treatment plants. These gangs are no match for your small- to mid-sized healthcare organization if they have become strong enough to destroy both military and civilian infrastructure. You're just a drive-by ATM to them.
According to the Huntress research, The State of Cybersecurity for Mid-Sized Businesses in 2023, about 25% of small and medium-sized businesses (SMBs) have either experienced a cyberattack in the last year or were unaware that they had. These days, cybercriminals are easy to spot. They're "blending into" your regular IT processes to take advantage of built-in system features because they've progressed beyond the stage of typical ransomware approaches.
This facilitates their ability to take control of and modify your systems through genuine programs like Remote Monitoring & Management (RMM). Living-off-the-land binaries (LOLBins), for example, are trusted executables that come pre-installed on your operating systems and can be used by cybercriminals. They also use the technology for malevolent purposes. Using anti-virus software or normal spam filters won't cut it if these threat actors aren't merely using unique malware. As a result, you require access to your complete security system.
These Are Some Solutions That You Can Use Right Now
Healthcare cybersecurity has significant risks, including the loss of life, so institutions like yours must take preventative and proactive measures. You need to implement a defense-in-depth strategy because it is no longer possible to have a safe single layer of security. This means building protections in layers using tools like threat detection, data encryption, intrusion prevention, patch management, and more.
Thus, if a danger manages to evade any of these defenses, an additional layer exists to prevent it from doing so. However, a layered strategy probably needs constant observation and adjustment. You can still accomplish effective protection using many low-tech options, even if you don't have the internal resources or knowledge to handle your cybersecurity.
Security Awareness Training (SAT)
To teach your employees cybersecurity best practices, introduce SAT. These courses, which can help them make more informed decisions to protect their company and their patients, can also contain phishing simulations and pertinent cyber threat training. It is recommended that you incorporate captivating, narrative-based courses into SAT programs since research has shown that these methods improve students' memory of the material.
Multi-Factor Authentication (MFA)
By requiring your employees to use a second verification factor—like a personal phone or a security token—to access an account, MFA adds an extra degree of security. You may have encountered MFA when logging into your preferred streaming service or banking app. MFA has the advantage over usernames and passwords, which are easily forgotten, lost, or stolen.
Managed EDR
For your healthcare company, this may be the most potent and economical option. Through the integration of cutting-edge technology and human-led analysis, a managed EDR handles crucial cybersecurity duties for you, such as:
- Monitoring and collecting endpoint data
- Detecting and investigating threats
- Triaging alerts
- Providing actionable remediation steps, including one-click solutions
Huntress Managed EDR is simple to implement and is overseen by a Security Operations Center that operates around the clock. From the moment you notice suspicious activity until remediation, these cybersecurity professionals are on your side.
Huntress Protects the Cybersecurity Requirements of Healthcare
You must maintain your defenses as fraudsters are targeting healthcare institutions. This is particularly critical in a world when budgets are getting smaller and threats are growing.
These days, cybercriminals are more cunning, well-coordinated, and unforgiving than ever. As long as they can make a quick profit, they don't care who they injure. To safeguard your company, your employees, and your patients, it is imperative that you strengthen your cybersecurity.
However, constructing a comprehensive defensive infrastructure calls for a substantial amount of money, materials, and knowledge. Prioritizing these can be challenging for smaller healthcare institutions, but there are ways around it. Consider any possible hazards. Inform your employees about online dangers. As in medicine, even the most basic preventive measures can halt the spread of something far more dangerous.
The Final Words
Cybercriminals are becoming a bigger menace to the healthcare sector, as phishing scams and ransomware attacks become more common. Due to a lack of skilled cybersecurity experts, outdated equipment, and limited resources, small to mid-sized healthcare institutions are especially vulnerable. Even bigger challenges come from state-sponsored cybercriminals and advanced persistent threats.
Healthcare providers need to implement a defense-in-depth approach that includes managed Endpoint Detection and Response (EDR) systems, multi-factor authentication, and security awareness training to lessen these risks. Healthcare institutions may safeguard their staff, clients, and enterprises from the increasing number of cyberattacks by making cybersecurity a top priority.