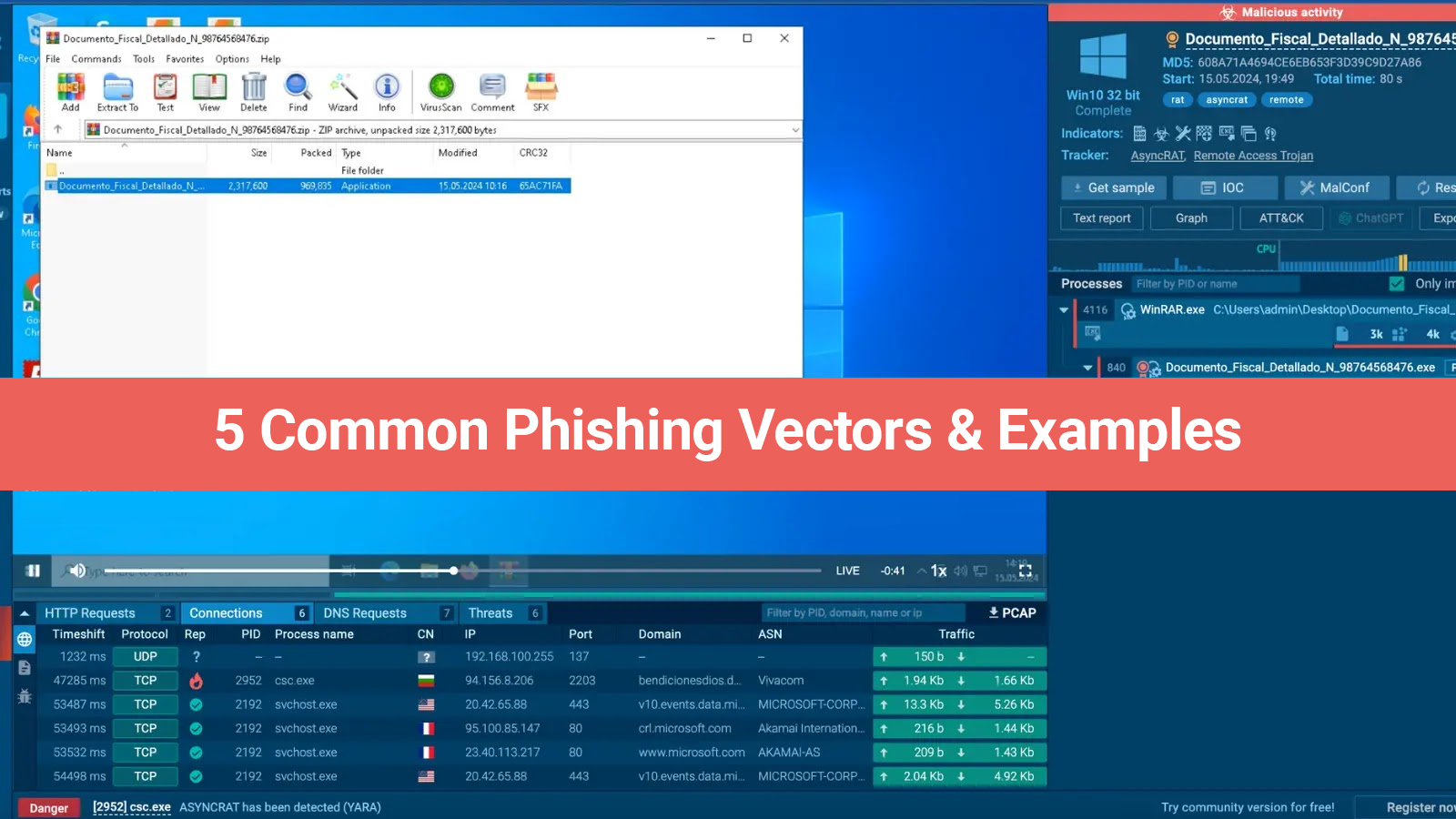
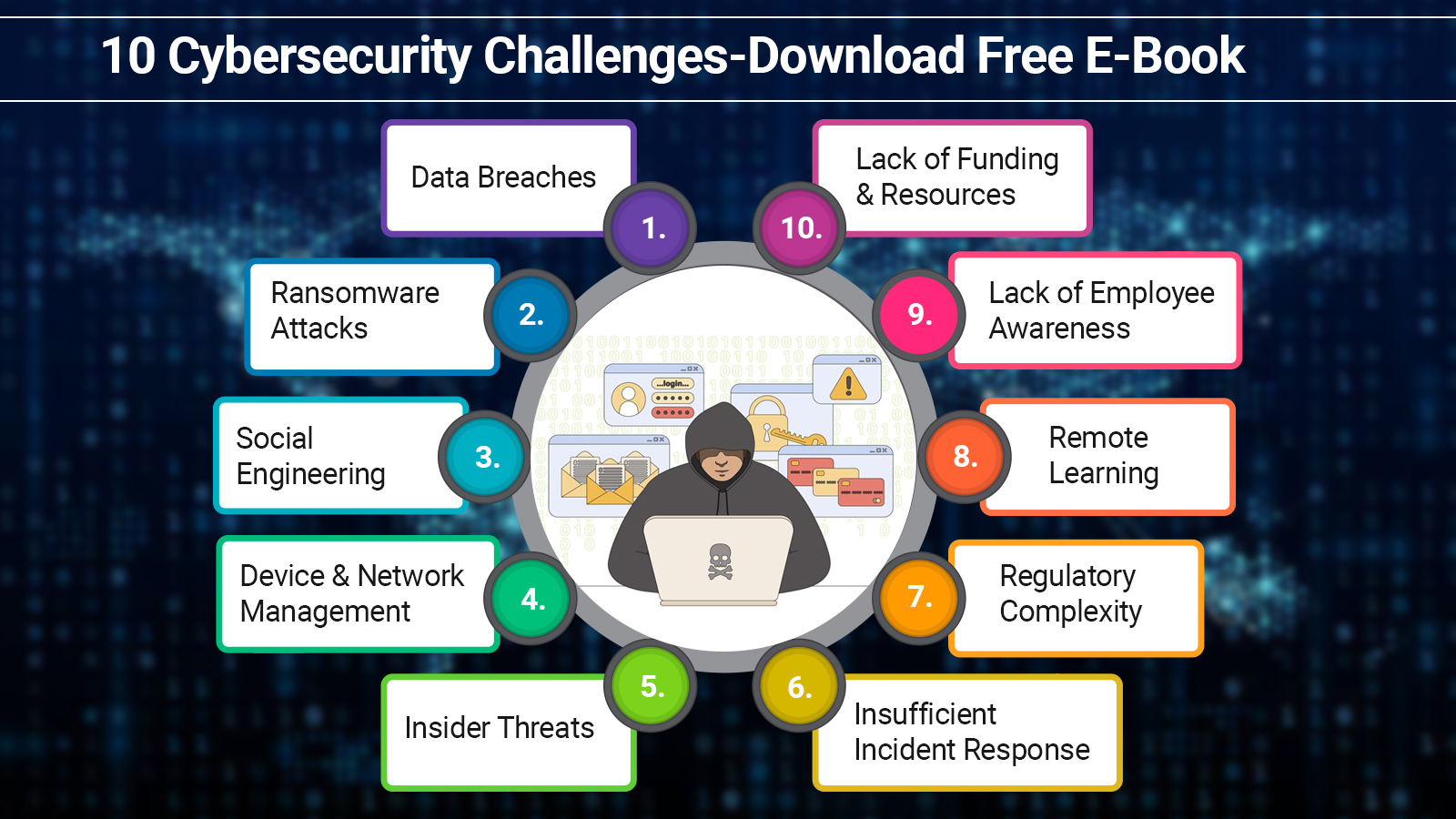
Fraud and email hacking are now frequent occurrences. If mail accounts are not secured, cybercriminals can quickly access them and take over. They can accomplish this through data breaches, phishing attempts, and weak apps. Every day, over 347.3 billion emails are sent worldwide, many of which include sensitive information.
Over 3.4 billion phishing emails are sent out daily by fraudsters, who use a range of tactics to make the emails look real. Using email security header best practices can help strengthen your online defenses. You must be conscious of the attacks that you are facing. Encourage team members to be aware of this and handle passwords with caution.
Meaning of Email Security Headers
Email security headers are made up of invisible components. These concealed sections include vital information that both identifies and authenticates transmissions. Since they offer protection against attacks, they are crucial components of the protocol.
Security headers provide information about the message's integrity and source. By implementing email security best practices, you can be sure emails don't leak your data. The defense in real-time helps your squad.
You stop fraud before it affects your company. Cybercriminals aim to take complete control of your email correspondence. Best practices for email security can stop and manage assaults. Organizations can maintain the security of their mail communication by using various tactics.
Encrypt Emails
One form of authentication that keeps unauthorized individuals from reading your message while it's being delivered is encryption. Consider what a coded or disguised communication may look like to get an idea of what it means to encrypt an email.
The communication is rendered unintelligible by encryption. It wouldn't help a cyber-attacker even if they managed to access it. Understanding how to encrypt email is essential for anyone who communicates by mail.
It is particularly crucial when sending private correspondence. Various encryption techniques are needed for different email applications. Understanding how to encrypt email in each is essential. Learn how to encrypt an email in Gmail and send an encrypted email using Yahoo.
Either utilize encryption software or encrypt emails directly on a mail application. Write the email before encrypting it using the application. After that, pick encrypted attachments and content and adjust the security settings.
If you wish to use third-party software, configure it while the program is being installed. You can select from a wide variety of encryption software kinds. Before utilizing the software, could you pay close attention to its security?
Understand the Mailing Threats You Are Dealing With
There are new threats every time you send or receive mail. According to research, since 2020, there has been a threefold rise in cyberattacks. People and institutions must be aware of the common assault types. They can then put the best mail security measures into effect. Some of the most common risks are listed here.
- Phishing Threats. Every day, cybercriminals send out over 3.4 billion phishing emails. What they want is your data.
- Malspam Threats. These are malware-filled spam emails. Cybercriminals affix attachments or links to them. Based on up-to-date data, offenders send out over 162 million spam emails every day.
- Spoofing Threats. Cybercriminals send phony-looking emails with certain attributes. Based on the statistics provided, around 30,000 spoofing assaults occur every day.
- Ransomware Threats. Your emails are encrypted by cybercriminals, rendering them unreadable. When the encryption is removed, they demand a ransom. According to data, there will be 37,700 ransomware attacks each hour in 2024.
Conduct the Best Password Management Practices
You can create, store, and use all your passwords using reliable password management software. It will improve password security & usability along with various other mail protection strategies. This helps in creating complex & unique login data. Moreover, you should also employ effective techniques to recollect the login information easily. For this, there are various email security recommendations, such as the following:
- Use Password Management Software: This software will help you manage all your login information from a single place.
- Create Complex Login Information: Make complex passwords that are much more difficult for anyone to crack down on.
- Don’t Share Your Password with Anyone: Share your passwords with reliable people only with those who truly need to know.
- Add an Authentication Layer: Add an extra security layer by using a multi-factor authentication protocol.
Conduct an In-Depth Employee Training Program
Every company should prioritize an employee training program to maintain system security and prevent cyberattacks. The training program will allow the employees to recognize the potential cyber threats and put an end to them. Here are some effective ways to support the employee training program about email security:
- Educate them about the dangers and their role in maintaining cyber security.
- Establish a culture where any suspect is reported right away.
- Act upon the report completion and identify the suspected individual.
- Set up phishing scenario(s) for your employees to learn from.
- Testing your employees’ understanding of how phishing works.
- Provide them with the necessary resources for maintaining secure communication.
- Track your employees’ development and the effectiveness of the training.
Implement Multi-Factor Authentication Protocol
Multi-factor email authentication protocols are operational techniques that enhance cyber security from the background. They guarantee the security of every incoming and outgoing mail. Multi-factor authentication protocols guarantee that the emails are legit. Certain emails may be blocked by the protocols or directed to the spam folder if they appear suspicious. Here are some authentication mechanisms that you can employ in your company:
- SPF (Sender Policy Framework): It compiles an approved IP address list, and blocks an email coming from a different IP address.
- DKIM (Domain Keys Identified Mail): It adds digital header signatures by receiving servers to confirm email authenticity.
- TLS (Transport Layer Security): TLS encrypts email security during delivery to guarantee the system’s complete safety.
- DMARC (Domain Message Authentication Reporting and Conformance): DMARC uses SPF & DNS to confirm the email senders’ authenticity.
Add Brand Logo to Emails
Enhancing your users’ trust through logo branding is crucial. Email open rates have significantly increased in the past few months and more professional appearance due to recognizable logos. It is easier for receivers to identify an email sender if it has a verified logo. It reduces the likelihood of clicking on malicious & phishing emails. Most recipients will open their emails when they have faith in the brand.
Return on Investment rises due to the brand's increased internet traffic. Companies must keep their mail structure consistent with their logo. You can include the logo in the sender ID picture, footer, or email header. You should include a well-designed logo in an email signature along with the correct colors, letters, and symbols.
Moreover, it should also contain all relevant & important information, including a phone number, email address, and a contact person. Put a call to action to tell your recipients what to do if they require assistance. You should also include helpful links for your customers to place orders, make reservations, or browse an online store/catalog.
Implement Cyber Defense Mechanisms
Maintaining email security will help you protect your system and emails. These are activities that go beyond email standards, training, and passwords. They guard your system against violations not just with emails but with the entire system. The likelihood of threats is minimized when defenses are placed properly. Here are some crucial defense-related activities that you should carry out:
- Create a mail backup for every sensitive correspondence.
- Turn on spam & anti-malware filters in your email.
- Be watchful on all email accounts and regularly check for security.
- Install internet security and antivirus programs, like TTB Internet Security.
All Things Considered
Placing all your mail security into place helps shield you from unauthorized access. Email encryption & authentication are some examples of protection techniques. Give your staff instructions on email security and the appropriate safety equipment.
Apart from this, you should also realize the cyber attacks your company may face and how to avoid them. The entire company must adopt the best password management techniques.
Did you find this article interesting? Join our TTB Community on LinkedIn for more intriguing articles & updates.