A company’s cybersecurity strategy cannot be completed without the Security Operations Center (SOC). The proficiency of each SOC member determines its success level. Through this blog post, you will learn about a 5 Star Training Plan that will help you produce Junior SOC specialists. So, read it carefully:
Steps for Effective Jn. SOC Specialist Training
Go through the following steps carefully to understand the steps of the Junior SOC Specialist program properly:
Step 1: Refresh Security Knowledge
A Junior SOC Specialist’s training program starts with helping them review their cybersecurity basics. Review basic ideas including system, network, and application security in brief. Even though the expert may already be knowledgeable about them, a refresher can confirm their understanding and point out their areas of improvement.
At this point, prospective professionals will also receive an in-depth rundown of their primary responsibilities. These mainly include threat hunting, incident response, and threat intelligence. To aid in their education, suggested materials or courses of study are as follows:
- Certified Malware Analyst;
- Certified Ethical Hacker;
- CompTIA Security+; and
- Certified IT Security Professional.
Step 2: Introduce SOC Tools & Technologies
Learning how to use the company’s security tools & technology should be the focus of the second stage. Allow the learners to familiarize themselves with the equipment they will be using:
- The Intrusion Detection System (IDS);
- The Intrusion Prevention System (IPS);
- Firewalls; and
- Security Information & Event Management (SIEM).
They need to understand the complete security system and how their parts fit in. Start providing practical instructions on how to configure, manage, and decrypt data from these security technologies.
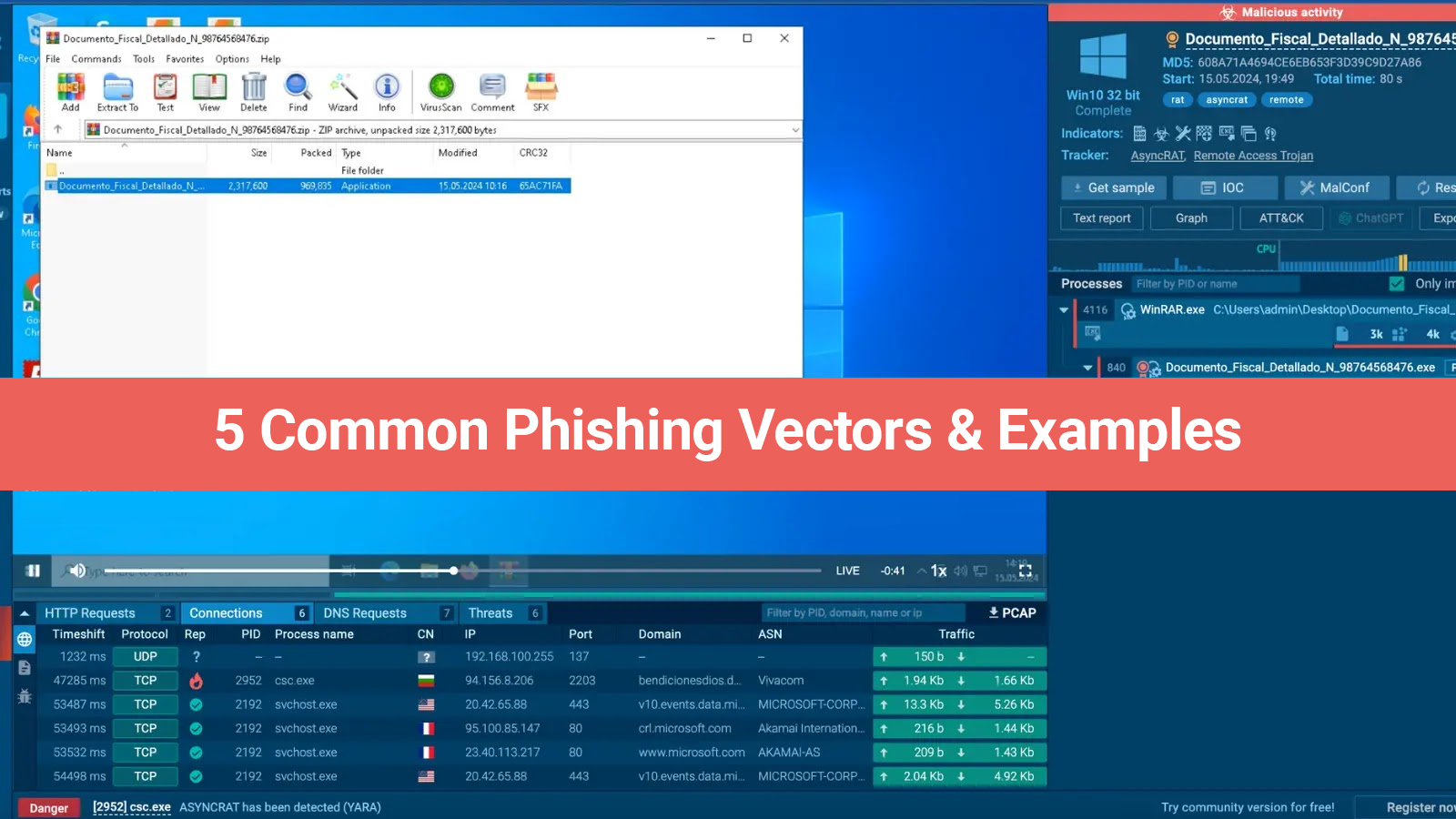
In addition to this, you should ensure that the learner can examine dubious files & links by this time. Also, they should be introduced to a sandbox haven where potentially dangerous software can be seen for this reason. For SOCs to analyze malware behavior without risking the company’s data infrastructure, a sandbox is a crucial tool.
Step 3: Strengthen Analytical Skills
To succeed in their positions, SOC specialists must have strong analytical abilities. To assist them in this way, you must offer:
- Tips & Strategies for Data Analytics;
- Critical Thinking Exercises; and
- Problem-Solving Techniques.
Real-world case studies can be quite helpful as teaching resources, especially if they are based on occurrences that have really happened and directly influence your organization. These situations can teach the use of analytical abilities in a SOC setting. Including the use of a sandbox can also be a successful tactic. Sandboxes provide an in-depth timeline of an attack, allowing security experts to note:
- Impact on the Infected System;
- Registry Activity;
- Active Processes; and
- Network Connections.
The junior analytics capability of evaluating cyber attacks and determining the best counter-action for security can be improved to a great extent by having a detailed understanding of the malware execution process.
Step 4: Offer Practical Experience
Next, give enough opportunities to the analysts to develop experience by allowing them to work under senior colleagues’ supervision in a real-life SOC scenario. Internships & on-the-job training are 2 different ways to accomplish this. The analysts must start using their analytical abilities, using a sandbox for analysis, and using SOC Tools & technologies.
Step 5: Promote Continuous Learning
As cyber threats are constantly evolving, SOC specialists should also engage in a never-ending learning cycle. Motivate the analyst to study the latest developments in the danger scene. This will improve the specialist’s ability to recognize emerging threats, use security technology, and stay updated with the industry's best practices. Provide them with a list of helpful resources, such as online blogs & forums about cybersecurity, to make this process easier.
Use ANY.RUN to Streamline SOC Workflow
A cloud-based sandbox called “ANY.RUN” was created to make security team communication more efficient. Working on a private setting allows users to:
- Conduct Malware Analysis;
- Easily Extract IOCs;
- Share their Findings; and
- Check the Junior Specialists’ Work/
Users may operate the analytical environment just like on a computer, opening files, executing programs, and starting the systems. All these are possible due to an interactive user interface. This is highly beneficial for experienced professionals to perform in-depth investigations as well as Junior Specialists who are receiving practical training.
All Things Considered
The development of capable junior specialists for the Security Operations Center (SOC) is the center of this post. The plan calls for updating cybersecurity knowledge, introducing SOC technologies, and strengthening analytical capabilities.
Moreover, it also provides real-world experience and encourages lifelong learning. Using a focus on practical training and the application of tools, this blog post seems to equip Junior SOC Specialists to successfully address the ever-evolving cybersecurity threats.
Did you find this article interesting? Join our TTB Community on LinkedIn for more intriguing articles & cybersecurity updates.