Teaming is a form of ethical hacking technique that companies use to pen-testing their servers, networks, and systems Although many organizations consider prevention to be the ultimate form of security, detection, and repair are equally important parts of a comprehensive defensive strategy.
Hiring an ethical hacker serves the purpose of strengthening the cybersecurity defenses of the company by identifying vulnerabilities through a simulated attack and fixing them. In addition to blue & red teams, there are also many other teams, such as purple & white teams. Through this post, we'll examine the functions of these teams and how they support an organization's network analysis & improvement.
Different Types of Teams and Their Role in CyberSecurity
Explore the diverse roles of various teams in improving the cyber security defenses:
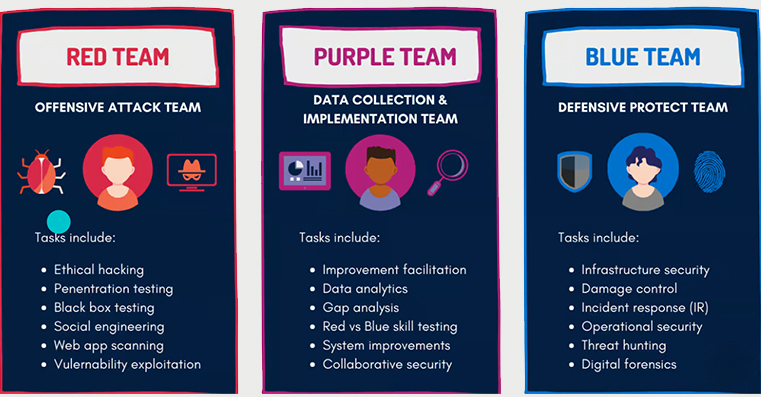
Red Team
“Red Team” is an intelligence-driven security assessment that thoroughly looks at an organization's cyber resilience, threat detection, and incident response capabilities. A red team is made up of security specialists who pose as opponents to circumvent cyber security measures. Red Team is the practice of ethical hackers using their criminals’ Tactics, Techniques, and Procedures (TTPs) to mimic the circumstances of an actual cyberattack.
Independent ethical hackers who equally evaluate system security typically make up red teams. To obtain unauthorized access to assets, they use every possible strategy to identify weaknesses in individuals, procedures, and technology. Red teams create ideas & strategies for strengthening an organization's security posture based on the data they obtain from these mock attacks.
A red team includes cyber experts who covertly test a company's security measures. Usually, they have no connection to the business (target). The team is made up of skilled, moral hackers whose goal is to find and safely exploit vulnerabilities in the target's physical or cybersecurity perimeters.
An organization's weaknesses & security risks are revealed, assumptions are tested, alternate attack strategies are examined, and vulnerabilities are analyzed by the team. Moreover, it assesses your company’s security posture to see how well it will fend off threats in real time before they materialize.
Red Team is a term used to describe a group of individuals’ exercises where the attackers do certain tasks. Usually, it gains early access by obtaining user credentials or by using social engineering methods. To penetrate the network as deeply as possible without being discovered, the red team increases its privileges and moves laterally across systems while inside it.
Traditional penetration testing techniques, such as those used by vulnerability scanners like Nessus, use noisy procedures to find security flaws. Contrarily, a red team is known for operating in stealth and will do everything it takes to stay hidden. Certain businesses will rely on their systems.
The job of red teams is to break into different systems and assess how secure they are. The strategies used by a red team include impersonation as well as conventional phishing and social engineering assaults on staff members. Technically & artistically gifted, a red team member should be able to take advantage of both human nature and system weaknesses.
Blue Team
A blue team consists of cyber security experts with an organization’s insider knowledge. Their responsibility is to protect the company's most valuable assets from getting harmed. They are knowledgeable about the organization’s security plan & business objectives. Their task is to protect the castle walls to prevent attackers from getting past the defenses.
The blue team defends when the red team strikes. Experts in incident response typically make up this group, providing guidance to the IT security team on areas for improvement to prevent complex cyberattacks. Defending the internal network against various threats falls to the IT security staff.
The task of locating hackers and preventing them from accessing the company's network falls to the Blue Team. It analyzes the situation & protects the areas where an attack may take place. Their goals are to identify breaches quickly, contain the virus by limiting it to the system, and terminate the attack in real time.
In certain situations, the Blue Team can also plan and carry out recovery operations. Internal security teams, or "Blue Teams," protect against Red Teams as well as lawful attackers. The goal and perspective of a true Blue Team is to be constantly vigilant against attacks, and this is why most security operations teams don't have it.
For this reason, this team in an organization should be kept apart from traditional security teams. A “Blue Team" is typically housed in a Security Operations Center (SOC) which consists of highly skilled analysts. They work around the clock, seven days a week, to secure and protect their organization’s defenses.
Companies can also install automated technology on the network perimeter to neutralize many of today’s risks, like phishing emails. Proactive & reactive, the blue team provides invaluable human intelligence to aid the technology & tools. As a result, the team can identify & eliminate the most complex dangers.
Purple Team
The purpose of the Purple Team is to improve the Red & Blue teams’ effectiveness. They create a coherent story that optimizes both by combining the Red Team's threats & vulnerabilities with the Blue Team's defensive tactics & controls.
The Purple Team acts as a security strategy wherein red & blue teams collaborate closely to share information and give regular feedback to maximize cyber capabilities.
By creating realistic imitations of common attack situations and encouraging cutting-edge methods’ development for preventing & identifying new threats, Purple Team may assist security teams in enhancing vulnerability identification, threat hunting, and network monitoring.
Businesses use this team as a one-time, focused engagement with well-defined security goals, timelines, deliverables, and a systematic approach to evaluating lessons learned during an operation. Establishing an effective security monitoring role is difficult since it involves identifying both defensive & offensive weaknesses and outlining future technology & training needs.
The purple team acts as an improvised organization that is in charge of supervising & enhancing the red & blue team exercise. Usually, senior security officials or security analysts in an organization make up this group. Similar to a coached battle, Purple Team Exercises combine the Red and Blue teams for a pre-arranged exercise that combines testing & remediation in one location.
Purple Team Exercises typically involve more than just the quickest way to catch up with your defenses. Analogous to Tabletop Exercises, during the engagement the Red Team will replicate multiple Tactics, Techniques, and Procedures (TTPs), initiating an attack and waiting for the Blue Team to indicate detection & response to that particular attack style.
As a result, they can identify any vulnerabilities or gaps in detection & response, and quickly support issue remediation. Therefore, you know that dials are being altered and have a better idea of what has to be done when you depart.
White Team
The White Team contributes to the development of a company's operational security procedures, criteria for assessing progress, and rules of engagement. Typically, the White Team gathers lessons learned, carries out the post-engagement assessment, and communicates the discoveries. The responsibility of the White Team is to manage a battle between a Red Team of fictional attackers and a Blue Team of actual defenders of their company's computer systems.
In an exercise, the White Team acts as a judge, enforcing the rules, monitoring the activity, tallying teams, resolving any issues that may come up, responding to all inquiries or requests for clarification, and ensuring the competition goes without a hitch and doesn't obstruct the defender's mission.
The White Team contributes to the development of the engagement's operational security procedures, metrics for assessing progress, and rules of engagement. Typically, the White Team gathers lessons learned, carries out the post-engagement assessment, and communicates the findings.
The Bottom Line
This blog explores the crucial responsibilities that different teams play in boosting cybersecurity defenses. Red & blue teams evaluate & develop an organization's security posture by imitating attacks and fighting against them using ethical hacking techniques.
Furthermore, white teams supervise drills, assess performance, and promote communication for ongoing development, while purple teams maximize cooperation between red and blue teams. In the current digital environment, it is essential to comprehend these team dynamics to improve cybersecurity resilience.
Did you find this article interesting? Join our TTB Community on LinkedIn for more intriguing articles.