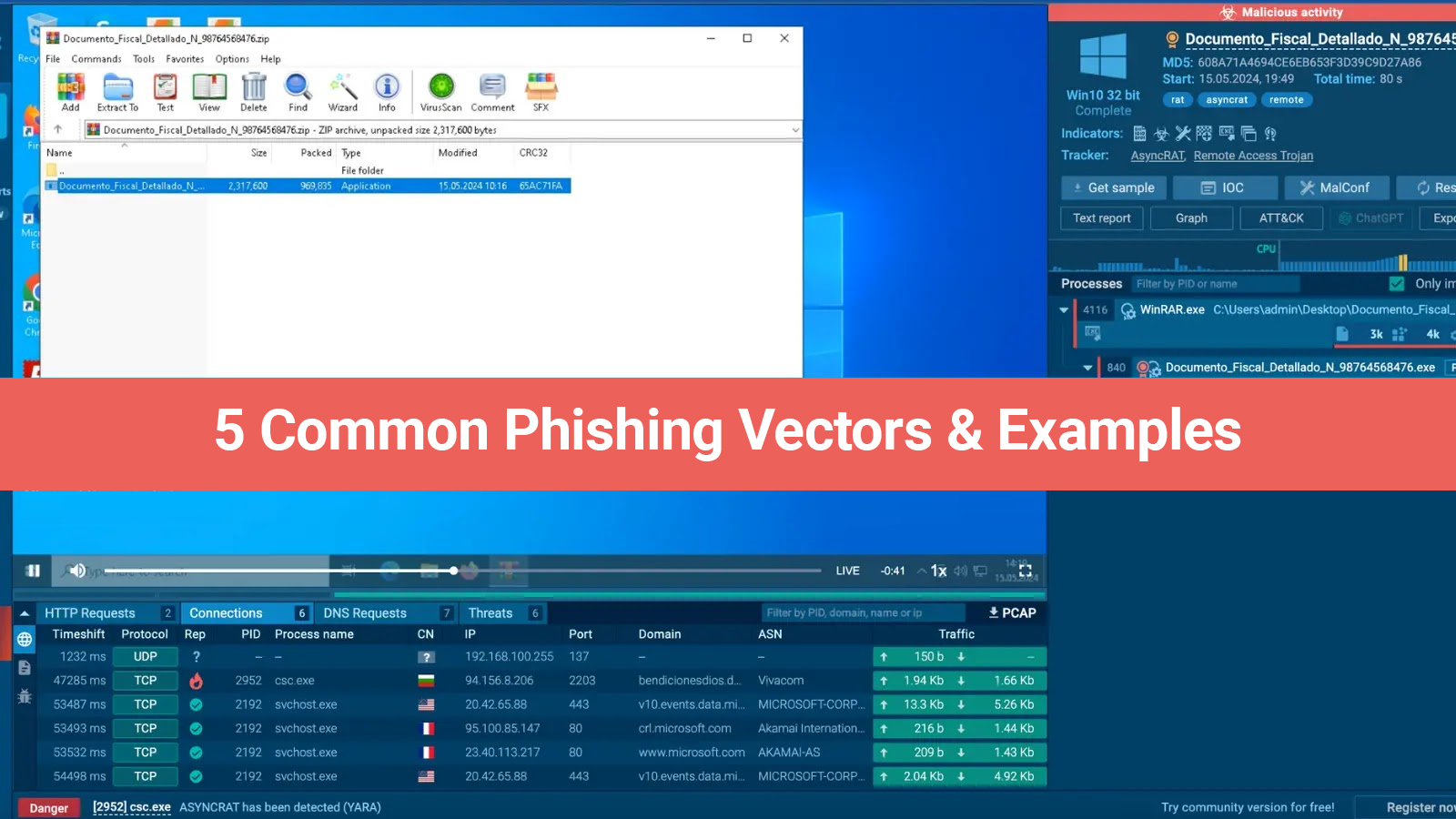
Cybersecurity risks are not limited to governments and large-scale businesses; small companies are vulnerable to them as well. There is considerable proof that small-scale businesses are more susceptible to cyberattacks, in part due to their lack of the resources necessary to defend themselves.
It is critical to protect your company from cyberattacks, but knowing where to begin can be difficult due to the ever-changing nature of cyberspace. Through this blog post, you will learn how you can navigate your small-scale business in the world of online threats.
Importance of Cyber Security for Small Businesses
Cyberattacks expose your finances, data, and IT hardware to several types of attacks. If a hacker manages to get into your network, they could exploit what they find to significant damage, such as the following:
- Access to your customer lists
- Your customers’ credit card information
- Your company's banking details & pricing structure
- Your company's product designs & business growth plans
- Other types of intellectual property like manufacturing processes.
These attacks endanger more than just your business. Hackers might use your network access as a launching pad to access the networks of other businesses whose supply chains your company is a part of.
As a result, the importance of cyber security for businesses has increased because more people work remotely globally. Small-scale companies are using cloud-based tools & technologies in their day-to-day operations.
Its principal components are online meetings, advertising, purchasing & selling, corresponding with suppliers & customers, and banking transactions. It is important to safeguard your data & cloud-based systems against unwanted breaches or hacks for reasons related to finances & reputation.
Impact of Cyberattacks on Small-Scale Businesses
The consequences of a hack could be disastrous for your company. It is a fact that 60% of small firms that experience an attack close down 6 months following the breach. Although it might be the most severe outcome of an attack, there are other repercussions that your company might face, such as:
- Financial losses from theft of banking information
- Financial losses from disruption of business
- High costs to do away with your network with the cyber threats
- Harm to your reputation following disclosure to clients that their data was hacked.
Cybersecurity Tips for Small-Scale Businesses
Small businesses may feel powerless when they encounter cyberattacks. Fortunately, you can take action to safeguard your organization by staying up to date with the most recent security concepts for organizations. Here are some crucial indicators of corporate cybersecurity:
1. Train Your Employees
Employees may depart, leaving your company open to cyber-attacks. Although exact figures differ by nation & business sector, it is certainly true that insiders are responsible for significant data breaches when they unintentionally or purposefully allow thieves access to your networks.
Attacks initiated by employees could occur in a variety of circumstances. An employee might misplace a work tablet or divulge login information, for example. Workers could also inadvertently click on phishing emails, which could infect the network of your company with viruses.
Consider providing your staff with cybersecurity training to guard against internal dangers. For instance, instruct employees on how to recognize phishing emails and the value of using secure passwords. Establish clear guidelines for the appropriate management and security of customer information and other sensitive data.
2. Carry Out Risk Assessment
Assess possible threats that could threaten your business’ information, systems, and network security. Identifying & evaluating potential cyber risks will assist you in creating a plan to close security holes.
Control the access of your company data and where it is stored as a part of your risk assessment. Consider who could be interested in accessing the data and how they could do so. If the data in your business is stored on the cloud, you can ask your cloud storage provider for help with your risk assessment. Assess the risk levels of future events and the possible impact of security breaches on your company.
After this research is finished and threats have been identified, use the data you have gathered to create or improve your security plan. Every time you make modifications to the way you store and use information, go over and revise this method. This ensures that the security of your data is maintained at all times.
3. Use Reliable Antivirus Software
Choose a reliable antivirus software that can defend your devices against ransomware, spyware, viruses, and phishing scams. Ensure the software has features that assist you in cleaning devices as needed and returning them to their pre-infected form in addition to protection. To protect yourself from the newest online threats and to fix any vulnerabilities, it's critical to keep your antivirus software updated.
Regularly Update Your System Software
The software you use to run your business, including antivirus software, needs to be updated at regular intervals. Software vendors frequently patch security flaws in their products or upgrade their software to make them stronger. Recall that certain software, like the firmware on a Wi-Fi router, may need to be updated manually. The router and your devices connected to it remain susceptible in the absence of updated security fixes.
1. Regularly Back Up Your Files
Does your business maintain file backups? Data loss or modification is possible due to a cyberattack. Could your business continue to operate in such a scenario? Remember to account for the volume of data that may be kept on smartphones & laptops; without these, many firms would not be able to operate.
Use a backup software that copies your files to storage automatically to assist. You can use your backups to restore all of your files in the event of an attack. To avoid having to remember to perform the backup procedure, select software that allows you to schedule or automate it. Keep backup copies offline to prevent them from being encrypted or rendered unusable in the event of a ransomware attack on your computer.
2. Encrypt Your Important Information
Having an encryption mechanism in place is a smart idea if your company often handles sensitive data, such as bank account and credit card information. Data is protected via encryption, which converts data on the device into unintelligible codes.
The worst-case scenario—in which your data is stolen—is what encryption is designed to survive. As a result, the hacker would be unable to utilize it as they would not have the necessary keys to decrypt & interpret the data. That is a sensible security safeguard in an environment where billions of records are exposed every year.
3. Limit Access to Sensitive Data
Limit the amount of your employees that can access the vital information. This will reduce the chances of data leaks and decrease the possibility that workers acting disloyally will be granted access to data. Carry out a plan outlining who can access what information at what level so that everyone knows their roles and responsibilities.
4. Secure Your Wi-Fi Network
Ensure you update to WPA2 or above if your company is still using Wired Equivalent Privacy (WEP), as these versions offer increased security. You're probably still using WPA2, but make sure you double-check, as some businesses don't update their infrastructure.
By altering the name of your wireless access point or router, also known as the Service Set Identifier (SSID), you can prevent hackers from breaking into your Wi-Fi network. For extra security, you can use a complicated Pre-Shared Key (PSK) passphrase.
5. Introduce a Strong Password Policy
Make sure that every employee uses a strong password on their devices that have private data. A strong password consists of a combination of uppercase & lowercase letters, numbers, and special characters, and should be at least 15 characters long, if not longer. The more difficult it is to crack a password, the less likely an attack is to succeed.
Additionally, you must organize a policy requiring password changes regularly. Also, small-scale businesses ought to permit Multi-Factor Authentication (MFA) on the software & devices that their staff members utilize.
6. Use Password Managers
Strong passwords that are specific to each device or account get hard to remember very fast. One more thing that can slow down your staff is having to write long passwords repeatedly and remember them. Tools for managing passwords are therefore widely used by enterprises.
Your passwords are automatically generated by a password manager, which saves them and provides you with the username, password, and security question answers you need to access websites & applications. This implies that to access their vault of login credentials, users only need to remember a single PIN or master password. In addition, several password managers advise against using weak or frequently used passwords and prompt users to update them frequently.
7. Use a Reliable Firewall
Any business that has its physical servers can benefit from having a firewall since it protects both software & hardware. Another way a firewall functions is by discouraging or preventing viruses from accessing your network. As opposed to this, an antivirus targets software that has already been compromised by a virus.
Installing a firewall ensures that your business's network traffic, both inbound & outbound, is protected. It can prevent network attacks by hackers by blocking specific websites. It can also be configured to limit the transmission of private emails and sensitive data from the network of your business.
8. Use a Virtual Private Network (VPN) Software
For your company, a virtual private network adds an extra level of protection. Employees who work remotely can safely access your company's network with the help of VPNs. They accomplish this by creating a secure link between your home internet connection and the website or online service you need to access, through which they route your data & IP address.
They are especially helpful while utilizing potentially hackable public internet connections, like those found in coffee shops, airports, or Airbnb. Users can connect safely and prevent hackers from accessing the data they are attempting to steal by using a VPN.
9. Protect Against Physical Theft
Remember that hardware theft is a possibility in addition to network intrusions that require your attention. It is important to keep unauthorized people away from corporate equipment including computers, laptops, scanners, and so forth.
To recover the devices in the event of loss or theft, this may entail physically locking the device or installing a hardware tracker. Ensure every employee knows the importance of protecting any data they may have on their laptops or cell phones when they are out.
For extra security, think about making unique user accounts & profiles for devices shared by several employees. Setting up remote wiping, which allows you to remotely erase the data on a misplaced or stolen device, is also a smart option.
10. Don’t Leave Your Mobile Devices
Security issues arise from mobile devices, particularly if they have access to the business network or contain sensitive data. However, while companies are organizing their cybersecurity, they may forget about them. To prevent hackers from stealing your company’s sensitive data when a mobile device is connected to a public network, ask your employees to encrypt data, install security software, and password-protect their devices. Ensure you establish reporting guidelines for tablets and phones that are lost or stolen.
11. Ensure 3rd Parties Who Deal With You Are Also Secure
Be careful about other companies that might be given access to your systems, such as suppliers or partners. Also, check if they adhere to the same procedures as you. Never hesitate to do a check before allowing someone access.
What to Look for in a Cybersecurity Company?
Cybersecurity may not always be a small business's primary emphasis. It makes sense that you would require assistance with cybersecurity—you do, after all, have a business to manage. But how can one find out what features to look for in a cybersecurity company? The following are some crucial qualities to search for:
- Independent Tests & Reviews: A great marketing campaign & technical language from a cybersecurity company could fool you. Therefore, it's critical to look at independent tests & reviews. The top cybersecurity companies are eager to reveal the findings of testing their solutions.
- Avoid Cheaper Options: A company that comes in, installs software, and then leaves should be avoided. Furthermore, you can't get the protection you require from a company that says it just specializes in one area without providing extra products or assistance.
- Extra Support: You want a company that provides a respectable degree of support, regardless of whether a danger has been identified or you are experiencing difficulties backing up your files. Choose a business that simplifies cybersecurity, discovers answers to problems, and guides you through them.
- Growth Potential: A cybersecurity firm that can expand alongside your organization is what you need as it grows. Pay attention to firms that provide a wide range of business security solutions.
Although small business owners have several tasks to carry out, cybersecurity is currently at the top of the list. Thankfully, there are precautions you can take to safeguard your small business, and a reliable cybersecurity provider can assist in lowering your risks.
Did you find this article interesting? Join our TTB Community on LinkedIn for more intriguing articles & updates.