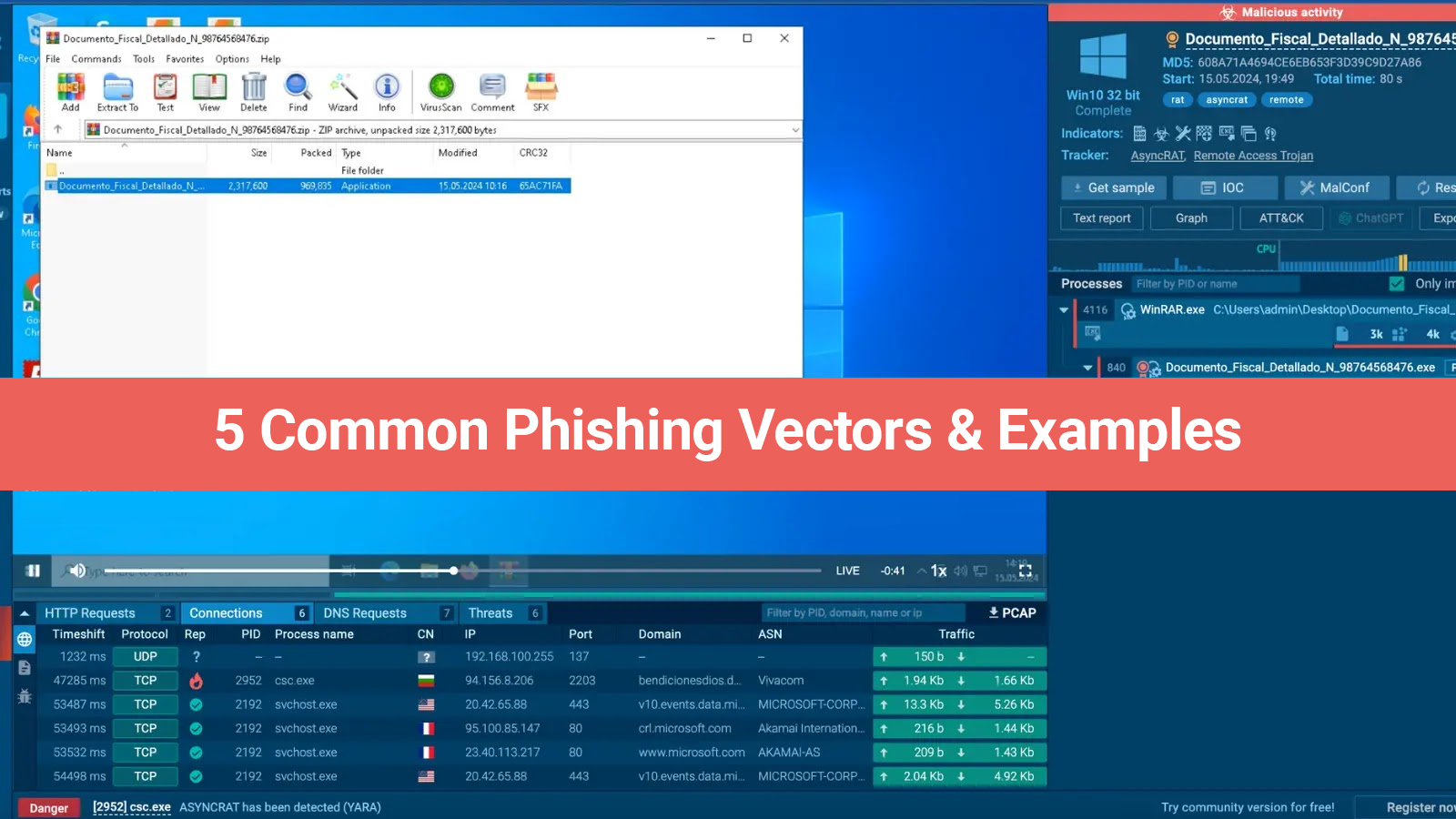
Due to linked devices, cloud services, IoT technologies, and hybrid work settings, today's security leaders have to manage an attack surface that is always changing and a dynamic threat environment. Since attackers are always coming up with new ways to attack, not every business can access the internal Red Teams or limitless security resources to keep up with the latest developments.
Not only that, but modern assaults are indiscriminate, so all businesses, no matter how big or little, must be ready. Security teams now need to foresee and prevent in addition to detecting and responding. Defenders must be quick and creative to tackle the security environment of today. To put it succinctly, we must begin to think like hackers.
By adopting the perspective of an opportunistic hacker and using reliable software (Like TTB Internet Security), you can enhance your comprehension of potentially vulnerable channels and prioritize your remediation efforts more efficiently. Moreover, it assists you in overcoming potentially damaging prejudices, such as the idea that your company is too little or uninteresting to be targeted. Let's take a closer look at these ideas.
The Hacker Mindset vs. Traditional Defenses
You can better identify possible exploitable channels by adopting a hacker's mindset.
The traditional approach to vulnerability management is adopted by many firms, which involves recording their assets and pinpointing related vulnerabilities, frequently according to a strict timetable. The fact that hackers think in graphs while defenders must think in lists is one of the issues with the current approach.
The first step for malicious actors is to identify their targets, and finding even a single avenue to access the royal jewels is important to them. Rather, advocates ought to inquire of themselves: Which assets trust and link to other assets? Is it possible for a hacker to penetrate a less vital system and utilize it as a means to breach a more crucial one? To be able to recognize actual risk, you must ask these questions.
Prioritizing remediation tasks more successfully can be achieved by adopting a hacker's mindset.
Selecting which concerns need to be addressed right away and which can wait is a difficult balancing act. Although few businesses have the resources to handle every attack surface at once, hackers are always searching for the simplest route with the most payoff. You can outperform bad actors if you know which remedial actions can block a possible route to your most valuable assets.
Prioritizing remediation tasks becomes easier when you approach them from the perspective of a hacker.
Smaller businesses frequently believe—erroneously—that opportunistic hackers won't find them appealing as a target. But the real world demonstrates otherwise. In small firms, there were 699 security events and 381 verified data leaks, according to Verizon's 2023 Data Breach Investigation Report.
In large businesses, there were only 496 incidents and 227 confirmed disclosures. Phishing assaults that are automated are not selective. Furthermore, at these smaller businesses, ransomware attacks can still be quite profitable. Any organization is a potential target when one adopts a hacker's mindset.
How Can a Hacker Think?
How can security experts successfully apply this change in perspective? Simply follow the methods explained in this section.
Understanding a Hacker's Tactics
Developing a hacker's mentality enables security leaders to identify possible sites of compromise and strengthen their defenses. This begins with a realistic comprehension of the methods that bad actors employ to travel from point A to point Z.
As an illustration, consider how current attackers leverage as much automation as they can to target the enormous number of computers on networks. This means that loaders, key loggers, exploit kits, and other quickly deployable strategies are just a few of the things that defenders need to be ready for.
In real-world situations, security teams must assess how they react to these strategies. While lab testing is an excellent place to start, firsthand evaluation of production systems is the only way to truly feel at ease. In a similar vein, while simulations are useful, teams also need to see how well their defenses withstand penetration testing and generated attacks.
Reveal Complete Attack Paths, Step by Step
There is never a vulnerability by itself. Almost invariably, hackers combine several vulnerabilities to create a comprehensive attack vector. Security chiefs therefore need to be able to test their whole environment and see the "big picture". Defenders can efficiently prioritize and remediate by identifying the critical channels that attackers could take from reconnaissance to exploitation and damage.
Prioritize Remediation Based on Impact
Usually, hackers seek out the least resistance. This implies that you should start by addressing your most impactful exploitable paths. As resources permit, you can go to progressively less probable scenarios from there.
The possible commercial impact of the vulnerabilities that need to be fixed should also be taken into account by leaders. A single user with excessive rights or a single network misconfiguration, for instance, can open up a wide range of attack avenues. Setting high-value assets and important security holes as your top priorities can help you stay out of the trap of dispersing your resources too widely over your whole attack surface.
Validate the Effectiveness of Your Security Investments
It is essential to test the practical effectiveness of security measures and goods. Is your EDR, for example, appropriately identifying suspicious activity? Is alerting occurring as expected from the SIEM? What is the response time of your SOC? The most crucial question is: How well do the various tools in your security stack work together? These assessments are crucial for gauging your level of effort.
Conventional attack simulation programs can evaluate known situations and assess how well your current defenses work against recognized adversaries. However, what about comparing your results to unknowns? You can autonomously test against all scenarios and risks by using the adversarial perspective. This can uncover hidden misconfigurations, shadow IT, or false assumptions about how controls might be operating. Attackers deliberately look for these undiscovered security holes since they are the most difficult for defenders to identify.
The results of validation tests must be communicated in a way that explains the business impact to the CEO and the board. It is insufficient to report on the proportion of vulnerabilities patched (or other vanity metrics) to accurately represent the efficacy of your security operation. As an alternative, you need to come up with more poignant ways to convey the results of your work.
Automated Security Validation Can Help You Stay One Step Ahead of Security Threats
We are aware of the difficulties in continuously evaluating & enhancing your security posture. The method of Automated Security Validation reliably tests your whole attack surface against real-world exploits to determine your security readiness against the most recent threats. Defenders may always feel secure about their security posture if they use tools and adopt the hacker mindset to continuously test their defenses.